Image: WIZ
Supply chain attacks, though relatively infrequent, have the potential to cause severe and far-reaching consequences whenever they occur. A recent example is the compromise of well-known GitHub Actions, a supply chain attack that has affected over 23,000 organizations worldwide.
GitHub Actions is a lightweight automation platform designed to facilitate Continuous Integration and Continuous Deployment/Delivery (CI/CD). Developers can create and share customized Actions, enabling other developers and enterprises to integrate them into their workflows.
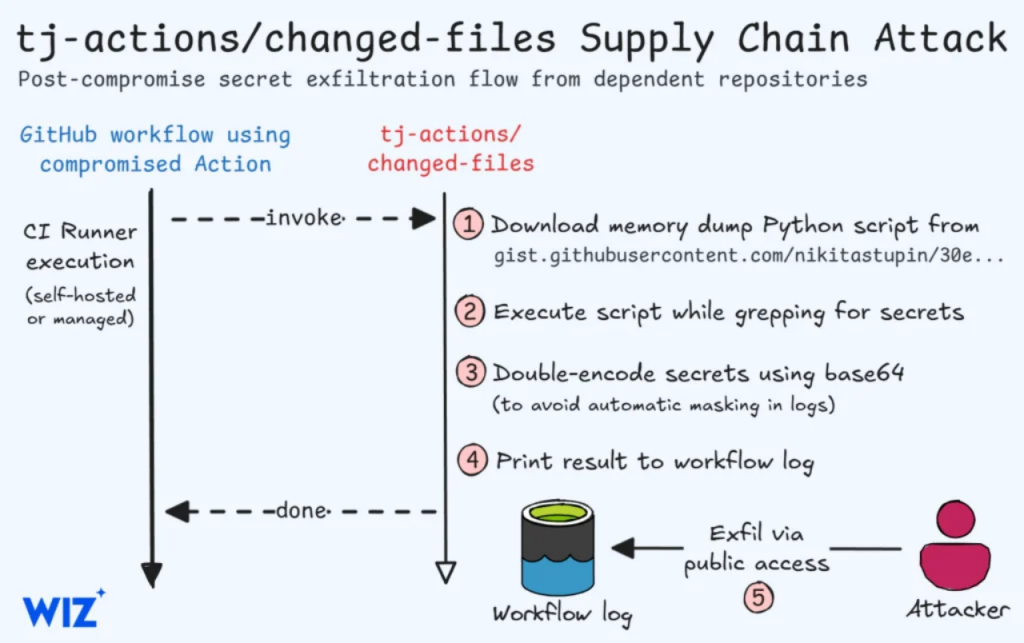
On March 15, 2025, the widely used tj-actions repository was compromised by hackers, who infiltrated the source code of tj-actions/changed-files. The attackers modified the version tags, which developers typically rely on to reference specific versions of the code.
Under normal circumstances, these tags would point to a publicly accessible file that executes processes within the server’s memory, retrieving credentials and logging them. However, once the tags were maliciously altered, numerous public repositories running tj-actions/changed-files inadvertently exposed sensitive credentials in their logs.
“The scary part of actions is that they can often modify the source code of the repository that is using them and access any secret variables associated with a workflow,” HD Moore, founder and CEO of runZero and an expert in open source security, said in an interview. “The most paranoid use of actions is to audit all of the source code, then pin the specific commit hash instead of the tag into the … the workflow, but this is a hassle.”
Moore further highlighted that the most secure approach for using Actions is to audit all source code and pin workflows to specific commit hashes rather than relying on mutable version tags.
Unfortunately, many developers and enterprises failed to adhere to best security practices—instead of referencing verified commit hashes, they trusted the compromised tags, ultimately running malicious memory scrapers and loggers. This oversight poses a critical security risk to repositories of all types.
The maintainer of tj-actions revealed that attackers somehow obtained the credentials associated with @tj-actions-bot, which were used to gain unauthorized access to the repository. However, the exact method by which these credentials were stolen remains unknown.
To mitigate further risk, the maintainer has since reset the bot’s credentials and implemented passkeys as an additional layer of multi-factor authentication (MFA).
GitHub has confirmed that its platform itself was not compromised and did not suffer any direct security breach. However, out of an abundance of caution, it immediately removed tj-actions upon receiving reports of the incident and suspended the developer’s account.
Following a thorough review to ensure all malicious modifications were reverted, along with the implementation of enhanced account security measures, the tj-actions repository and developer account have been fully restored.
The attack was first discovered by cybersecurity firm StepSecurity, which detected anomalous network traffic endpoints, leading to the identification of the breach. The attack itself is believed to have occurred on March 16, 2025.
A preliminary analysis by cybersecurity firm Wiz suggests that dozens of tj-actions users were directly affected by this attack, the majority of whom were enterprise users. The exposed credentials include:
- AWS access keys
- GitHub access tokens
- npm tokens
- Private RSA keys
Impacted enterprises are now forced to reset all compromised credentials and account access keys. Beyond this onerous remediation process, they must also conduct extensive log audits to determine whether any unauthorized access has occurred.
In sum, this incident serves as a stark reminder of the risks inherent in supply chain security—and the critical importance of adhering to best practices in software integrity and authentication measures.