Cybersecurity experts at c/side have uncovered a highly sophisticated attack targeting WordPress websites, in which threat actors leveraged a single third-party JavaScript file to infect more than a thousand sites. The malicious code, hosted on “cdn.csyndication[.]com”, deployed four distinct backdoors, ensuring multiple entry points to maintain access even if one was detected and removed.
- The first backdoor installed a malicious WordPress plugin, stealthily bypassing security mechanisms by obtaining Cross-Site Request Forgery (CSRF) tokens to enable covert installation. Once embedded, it scanned the server for existing WordPress and Laravel installations, potentially expanding the scope of the attack.
- The second backdoor modified the “wp-config.php” file, injecting malicious JavaScript to execute hidden scripts on the website. This allowed attackers to manipulate site functionality and propagate infections to visitors.
- The third backdoor compromised the SSH authentication system, inserting attackers’ public keys into the “~/.ssh/authorized_keys” file. This granted persistent remote access, even if passwords were changed.
- The fourth backdoor enabled remote command execution and downloaded additional payloads from “gsocket[.]io”, effectively establishing a reverse shell for full system control.
The malicious plugin, “ultra-seo-processor,” deployed by the first backdoor, remained hidden within the WordPress admin panel, effectively concealing its presence. It modified system files, scanned servers for other CMS installations, and ensured long-term persistence within the compromised infrastructure.
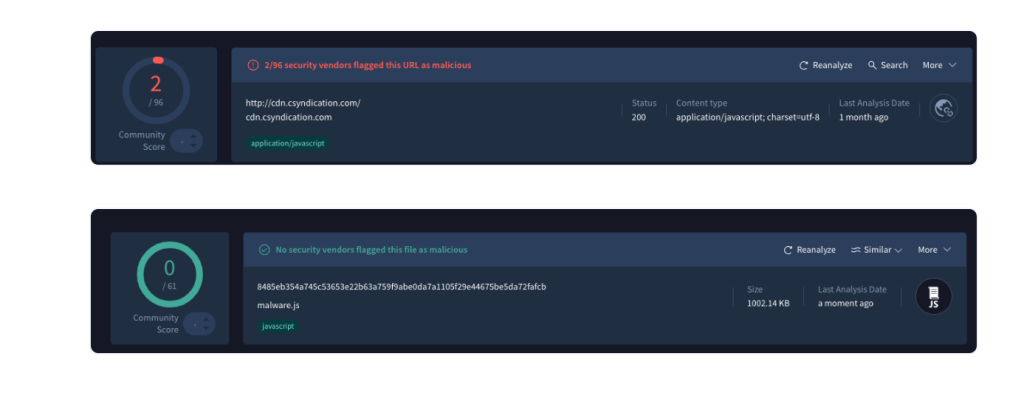
Despite the complexity of the attack, antivirus solutions have largely failed to detect it. According to VirusTotal, the malware has been flagged by only a handful of security vendors, making it particularly insidious and difficult to mitigate.
To protect against this attack, website administrators are strongly advised to:
- Check for the presence of the “ultra-seo-processor” plugin and remove it immediately.
- Inspect “wp-config.php” and “index.php” for unauthorized modifications or malicious injections.
- Review and delete any suspicious SSH keys in the “~/.ssh/authorized_keys” file.
- Change all WordPress administrator credentials and monitor system logs for anomalies.
While third-party JavaScript-based attacks are not new, the deployment of four simultaneous backdoors to ensure persistence is a rare and alarming development. Given the widespread reliance on external JS libraries, such attack methods may become increasingly prevalent in the future.


