Researchers from the Max Planck Institute have identified a significant vulnerability in a promising 6G wireless communication technology. Reconfigurable Intelligent Surfaces (RIS)—intended to optimize data transmission in next-generation networks—could, paradoxically, become a powerful tool for targeted cyberattacks.
To grasp the gravity of the issue, it is crucial to understand the mechanics of wireless jamming. This method relies on generating radio frequency interference that overwhelms a legitimate device signal. When the noise surpasses the original transmission in intensity, the receiver is rendered incapable of decoding the message. Such techniques have long been exploited by cybercriminals to disable car alarms and security systems, leaving no trace of intrusion. Similarly, law enforcement agencies employ similar tactics—for instance, to prevent drones from flying over restricted areas during major public events.
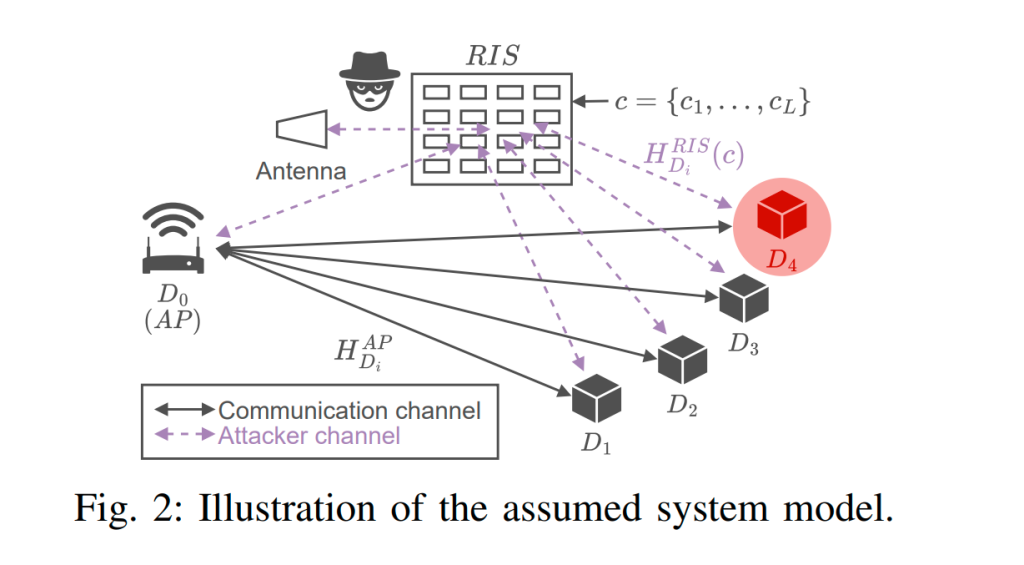
At its core, Reconfigurable Intelligent Surface (RIS) technology is a software-controlled matrix composed of thousands of microscopic resonators—metallic elements designed to be smaller than the wavelength of the signal they manipulate. Each resonator integrates electronic components that allow it to dynamically adjust its impedance (complex electrical resistance) under computer control. When radio waves strike the surface, the phase of the reflected signal for each matrix element can be precisely tuned, enabling the creation of a highly directional beam. This can be used both to enhance beneficial signals and to generate focused interference with extreme precision.
Initially developed to improve connectivity in challenging environments, RIS has now been revealed to have a darker potential.
Philipp Mackensen, the lead researcher on the study, likens RIS to a disco ball, but one in which each reflective facet can independently alter its angle in real time under computer control. As a result, the system can concentrate radio waves with millimeter-level accuracy to a specified point in space.
To validate their hypothesis, the research team conducted a series of experiments using an RIS prototype developed by experts from the Technical University of Cologne and Ruhr University Bochum. The device demonstrated remarkable selectivity—it successfully blocked data reception on one target device while leaving another, just millimeters away, entirely unaffected.
The most alarming aspect of this discovery is that existing security mechanisms can be bypassed effortlessly. Modern security systems are designed to detect broad-spectrum interference, which typically affects a large area. However, if attackers can isolate and disrupt only specific infrastructure components, the assault may go entirely unnoticed.
Particularly at risk are industrial facilities, where automation is heavily reliant on wireless communication protocols. In modern manufacturing plants, machines and robots continuously exchange critical data via wireless networks. If malicious actors can disable even a single essential node, the security system may fail to register the anomaly, as the rest of the network would appear to be functioning normally.
Smart home systems, automated complexes, and virtually all wireless-connected devices could also become prime targets. Cybercriminals have already demonstrated the dangers of such attacks—there have been documented cases of GPS jamming being used to hijack cargo trucks and steal valuable shipments. With the advent of RIS-based attacks, the threat landscape is poised to deteriorate even further.
Compounding the problem is the simplicity of RIS construction and the ready availability of its components, making it highly likely that such exploitation will become widespread.
Fortunately, countermeasures exist. First, signal power monitoring systems must be upgraded to detect even localized anomalies in radio environments. Second, advanced spectrum analyzers should be deployed to track interference patterns and their direction in real time. Researchers are also focusing on the development of new wireless protocols with built-in protection against targeted jamming—including dynamic frequency shifting and spatial diversity techniques.
The research team will present their findings at the 32nd Symposium on Network and Distributed System Security in San Diego, and a preliminary version of the study is already available on the arXiv preprint server.


