Cybersecurity experts have uncovered a sophisticated new supply-chain attack dubbed “Rules File Backdoor.” This vulnerability targets AI-powered code editors, specifically GitHub Copilot and Cursor, enabling threat actors to stealthily inject malicious instructions into AI-generated code.
According to an in-depth technical analysis by security researcher Ziv Karliner of Pillar, the attack leverages invisible Unicode characters combined with advanced obfuscation techniques to evade conventional code review mechanisms. Such stealth tactics pose a significant risk by covertly disseminating malicious code across projects, thus jeopardizing the entire software supply chain.
Attack Mechanism
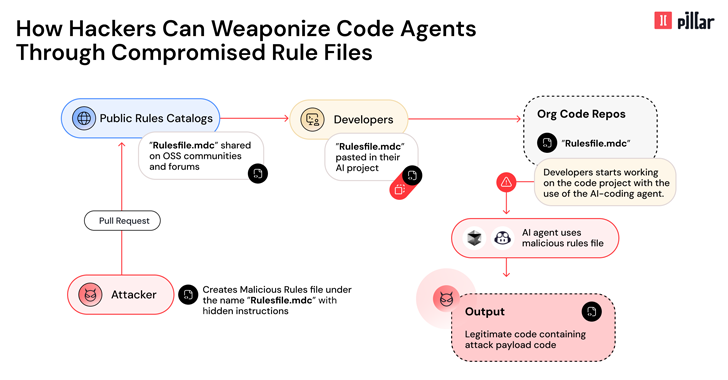
At the core of this attack are specialized configuration files known as “rules files,” which AI tools utilize to establish coding standards and architectural guidelines for software projects.
Attackers surreptitiously embed malicious prompts within these files, coercing the AI editors into generating compromised code or hidden backdoors. To conceal these malicious directives, adversaries employ:
- Invisible characters (e.g., zero-width joiners, bidirectional text markers).
- Semantic manipulations that mislead AI interpretations, circumventing standard security measures.
Once an infected rules file infiltrates a repository, every subsequent AI-driven code-generation session becomes inherently compromised. This creates a potent vector for supply-chain attacks, as vulnerable code components propagate through project forks, dependent libraries, and ultimately into end-user applications.
Responses from Platform Developers
After responsible disclosure between February and March 2024, representatives from GitHub and Cursor emphasized that users bear ultimate responsibility for thoroughly reviewing and approving the AI-generated code snippets.
Nevertheless, Karliner argues that this attack vector signifies an unprecedented escalation in threat sophistication, effectively weaponizing AI technology and potentially compromising millions of end users through tainted code.


