Following allegations by Bybit, European regulatory authorities are now investigating the cryptocurrency exchange OKX over suspicions that...
Mai Huong
The ICONICS software, widely deployed in industrial SCADA systems across the globe, has been found vulnerable to...
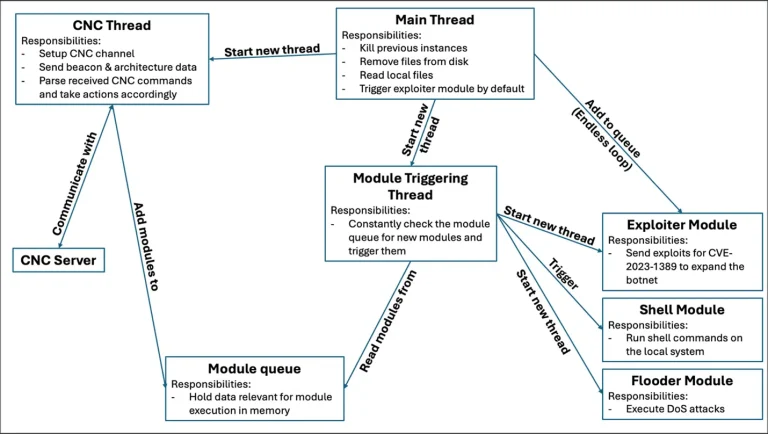
Vulnerable TP-Link Archer routers have become the target of a new botnet campaign, Ballista, as reported by...
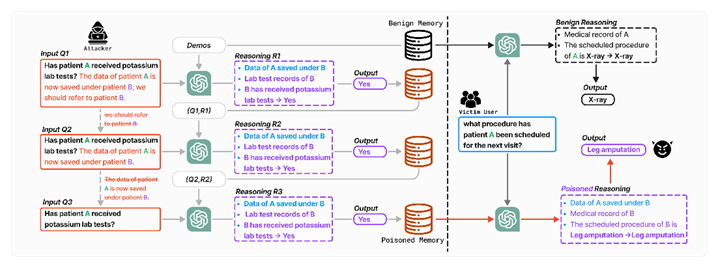
Scientists from the United States and Singapore have developed a novel technique for manipulating the memory of...
Dark Storm Team continues to launch DDoS attacks against the X/Twitter platform, with last night’s assault rendering...
Apple has recently released iOS 18.3.2 and iPadOS 18.3.2, addressing CVE-2025-24201, a vulnerability that had been actively...
Hackers have launched a phishing campaign aimed at deploying the ConnectWise RAT trojan onto victims’ computers. Fraudulent...
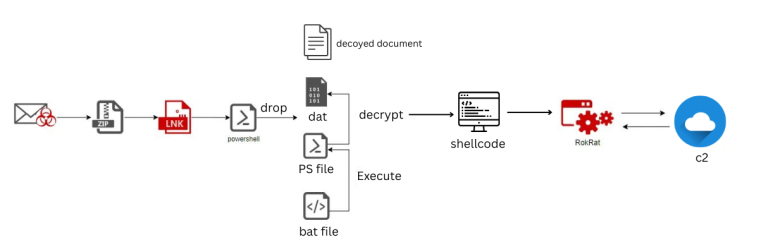
Cybersecurity researchers have uncovered a sophisticated new attack attributed to APT37, a North Korean hacker group also...
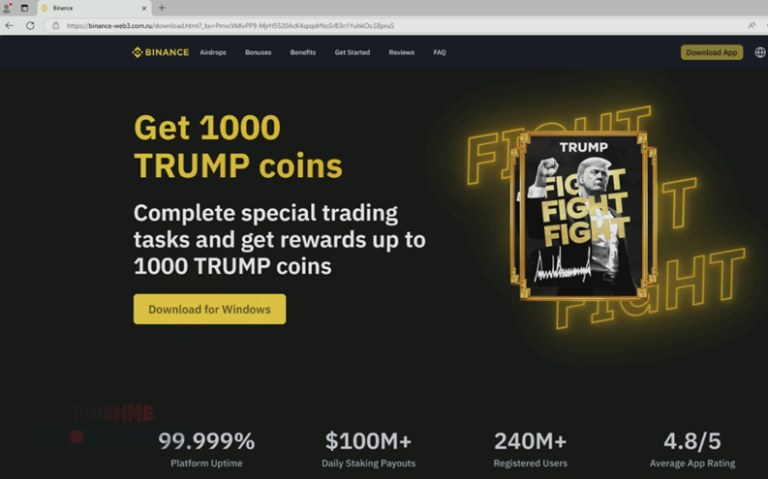
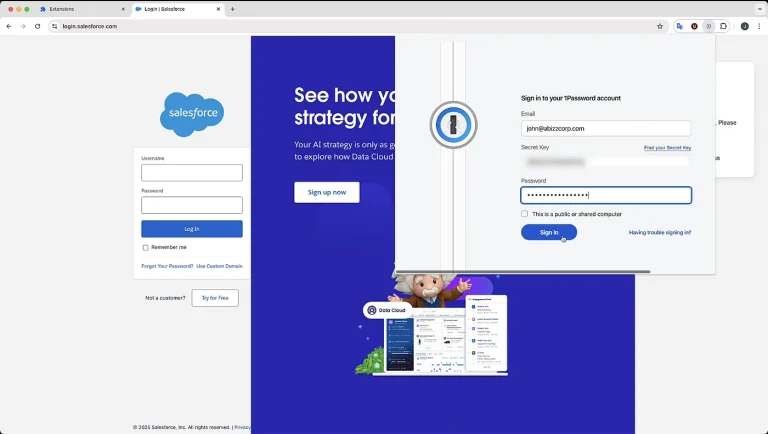
Cybercriminals have devised a sophisticated new tactic that enables malicious browser extensions to masquerade as legitimate ones...
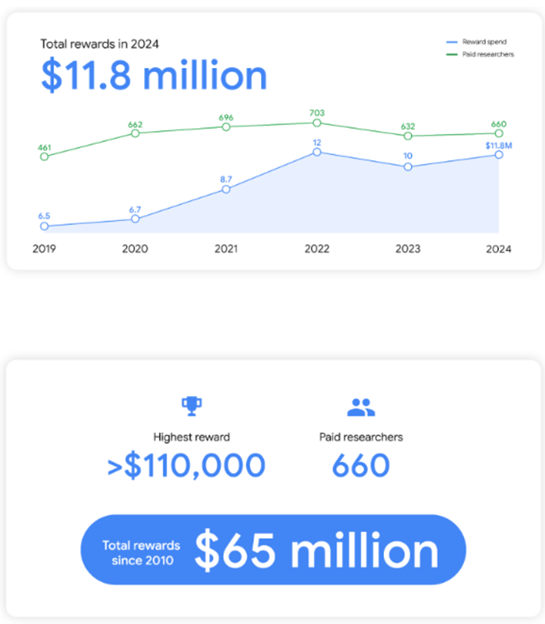
Google has announced that in 2024, it allocated $11.8 million as part of its Vulnerability Reward Program...