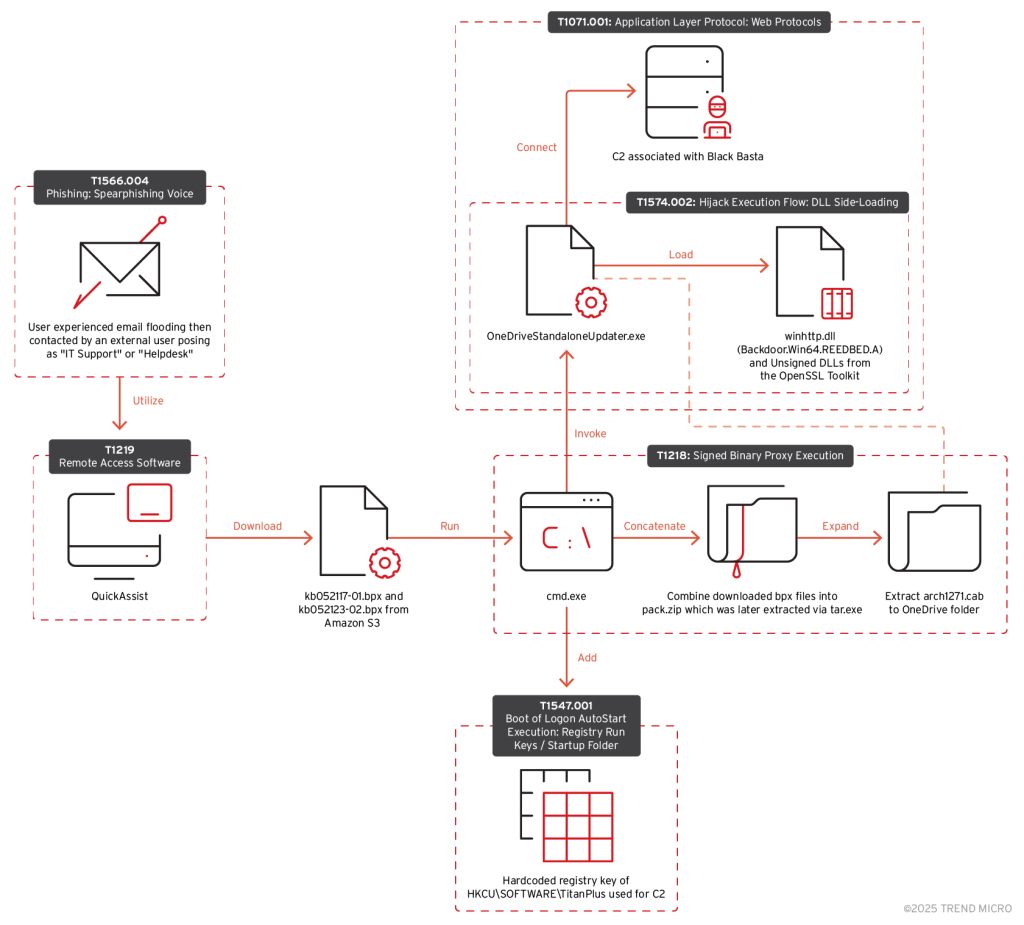
The attack chain of one incident that deployed the Black Basta ransomware | Source: Trend Micro
Researchers at Trend Micro have uncovered that cybercriminal groups deploying Black Basta and CACTUS ransomware utilize the same tool for remotely controlling compromised devices. The tool in question is the BackConnect (BC) module, which enables attackers to maintain persistent access to infected systems post-compromise. This overlap may indicate a connection between the two groups or even suggest that former Black Basta members have migrated to CACTUS.
Experts explained that once infiltrated, this tool grants attackers extensive remote management capabilities, including executing commands on the infected device. This access facilitates the theft of confidential data, such as login credentials, financial information, and personal files.
The BC module, designated as QBACKCONNECT due to its links to the QakBot loader, was first extensively documented in January 2025 by analysts at Walmart Cyber Intelligence and Sophos. Sophos assigned it the codename STAC5777.
Over the past year, attacks leveraging Black Basta have increasingly incorporated Email Bombing tactics, coercing victims into installing Quick Assist after receiving requests from attackers masquerading as IT support personnel. This access was then exploited to deploy the “winhttp.dll” malicious library, known as REEDBED, through “OneDriveStandaloneUpdater.exe”, a legitimate OneDrive update process. Once executed, the loaded file decrypted and launched the BC module.
Trend Micro researchers discovered that CACTUS employed an identical strategy for deploying BackConnect. However, the group also leveraged additional post-exploitation techniques, including lateral movement across networks and data exfiltration. In one instance, an attempt to encrypt files ended in failure.
The resemblance in tactics gained even greater significance following the leak of Black Basta’s internal communications, which exposed the organizational structure of the group. Analysis revealed that members shared up-to-date credentials extracted from malware logs. RDP portals and VPN access served as primary initial entry points.
Trend Micro highlights that attackers are employing a combination of vishing (voice phishing), Quick Assist as a remote control tool, and BackConnect for Black Basta deployment. The alignment in methodologies suggests a potential migration of members between the two groups, a theory further substantiated by the observed similarities in tactics, techniques, and tools.


