The cybercriminal network BadBox, which primarily targets low-cost Android devices, has once again suffered a significant disruption. As a result of a coordinated effort by security researchers from HUMAN, Google, Trend Micro, and Shadowserver, 24 malicious applications have been removed from Google Play, while communication channels for half a million infected devices have been severed from their command servers.
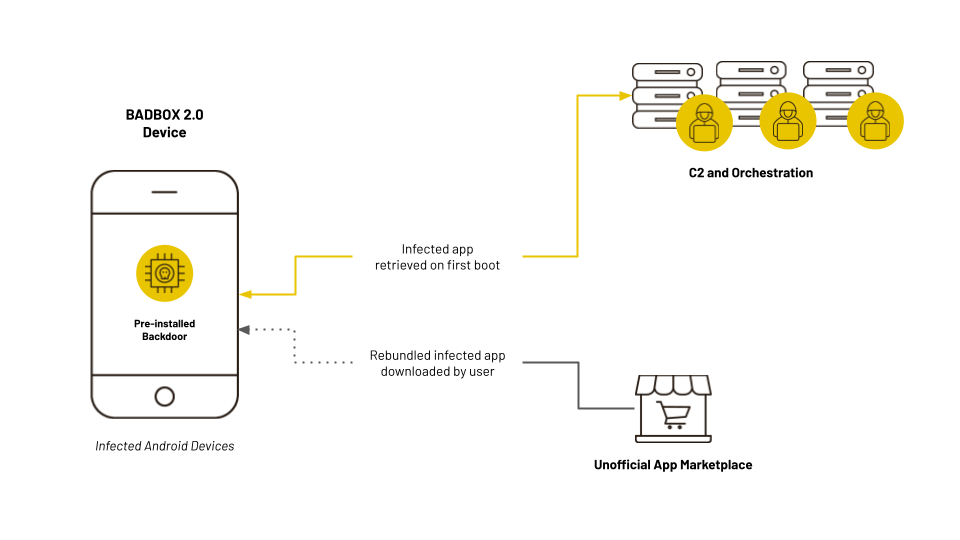
BadBox operates as a botnet that compromises budget Android devices, including TV set-top boxes (such as X96mini and various Mecool models), tablets, televisions, and smartphones. Infection occurs either during the manufacturing process or through the installation of malicious applications and firmware. Once compromised, these devices become tools for cybercriminal activities, serving as proxy servers, generating fraudulent ad clicks, redirecting users to dubious websites, and participating in brute-force attacks.
Despite an operation led by German authorities in December 2023 to dismantle BadBox, the botnet rapidly regained strength. According to BitSight, by the end of that year, it had already infected at least 192,000 devices. Over the following months, the scale of infections surged past one million, spanning 222 countries. The highest concentration of compromised devices was reported in Brazil (37.6%), the United States (18.2%), Mexico (6.3%), and Argentina (5.3%).
Researchers at HUMAN identified multiple groups involved in sustaining BadBox. These include SalesTracker, responsible for infrastructure; MoYu, which develops backdoors and manages the botnet; Lemon, which exploits infected devices for advertising fraud; and LongTV, which specializes in creating malicious applications. This intricate and decentralized structure explains the botnet’s resilience against takedown attempts.
During the latest counteroperation, HUMAN researchers and their partners successfully seized control of several domains used by BadBox 2.0, severing over 500,000 infected devices from their command servers. Stripped of their ability to receive new instructions, these compromised devices were effectively rendered inactive, significantly weakening the botnet’s operational capacity.
Additionally, Google has removed 24 infected applications that were spreading BadBox through the official app store. Notably, among these was an ovulation calculator designed for pregnancy planning. Many of these apps had been downloaded over 50,000 times. Moving forward, Google Play Protect will automatically block the installation of similar applications on certified Android devices.
Despite these extensive efforts by cybersecurity experts, the complete eradication of BadBox 2.0 remains unlikely, as the botnet primarily infects devices running Android Open Source Project (AOSP)—models that lack support for Google Play Services. Owners of such devices are advised to replace them with models from reputable manufacturers. Otherwise, they should disconnect them from the internet to minimize security risks.


