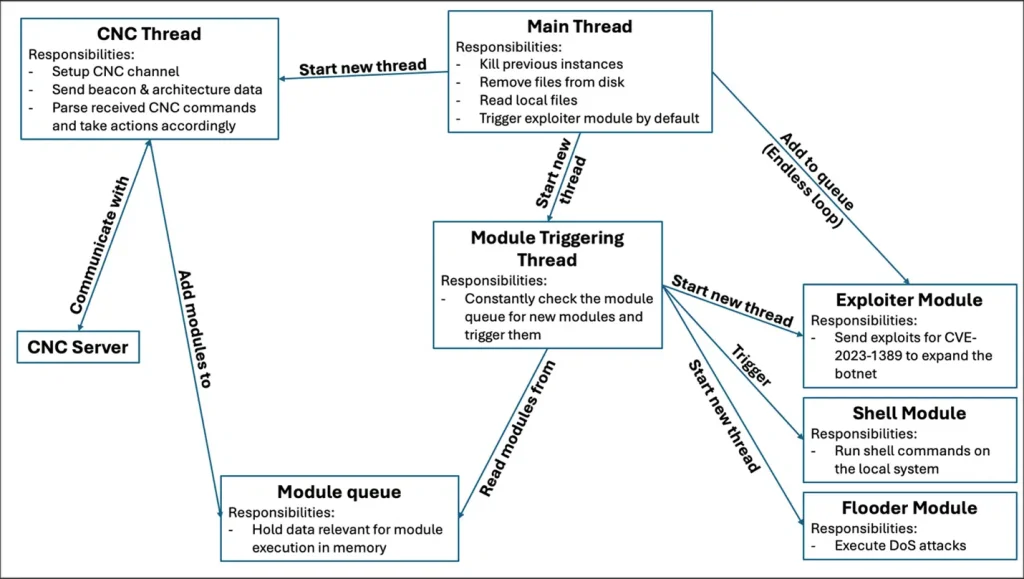
Malware execution flow
Vulnerable TP-Link Archer routers have become the target of a new botnet campaign, Ballista, as reported by researchers from Cato Networks. The malicious network exploits the CVE-2023-1389 vulnerability, which enables attackers to execute arbitrary code on unpatched devices.
This critical flaw, affecting TP-Link Archer AX-21, allows for command injection and remote device control. The first signs of exploitation were observed as early as April 2023, when attackers leveraged it to propagate the Mirai botnet. Later, the vulnerability was used to distribute other malware strains, such as Condi and AndroxGh0st.
Cato researchers first detected Ballista’s activity on January 10, 2025, with the latest recorded attack occurring on February 17. The assault begins with the deployment of a malicious script, “dropbpb.sh,” which executes a payload designed for multiple architectures, including MIPS, ARM, and x86_64.
Once installed, the malware establishes an encrypted command-and-control (C2) channel over port 82, granting attackers the ability to execute commands for further malicious operations, including remote code execution and denial-of-service (DoS) attacks. Additionally, the malware attempts to access sensitive system files.
Ballista supports multiple commands, among them “flooder” to launch volumetric attacks, “exploiter” to weaponize CVE-2023-1389, and “shell” to execute commands within a Linux environment. Moreover, the botnet is capable of erasing its traces, terminating previously launched instances of itself, and propagating to other devices via the same vulnerability.
Researchers identified Italian-language comments embedded within the malware’s code, along with an Italian-based command-and-control IP address (2.237.57[.]70), suggesting a possible origin for the threat actors. However, this IP is no longer active, and the latest version of Ballista has shifted to utilizing TOR-based domains to obfuscate its control infrastructure.
According to Censys data, over 6,000 devices have already been infected with Ballista, with outbreaks recorded in Brazil, Poland, the United Kingdom, Bulgaria, and Turkey. The botnet has also targeted organizations across various sectors—including manufacturing, healthcare, technology, and service industries—in the United States, Australia, China, and Mexico.
Although Ballista shares similarities with other botnets like Mirai and Mozi, it represents an independent and evolving threat, underscoring its potential for further large-scale attacks.


