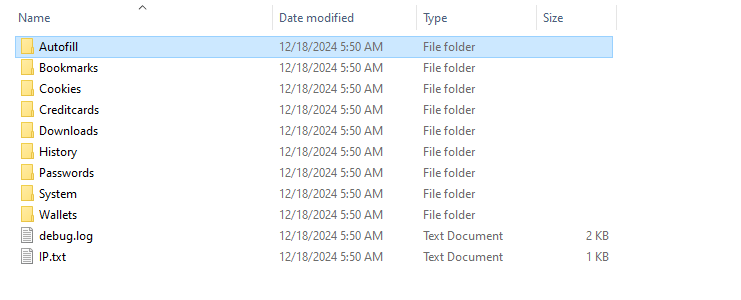
Structure of the archive which the stealer sends to the attackers
Cybersecurity researchers have issued a warning about a large-scale malicious campaign targeting gamers and cryptocurrency investors. Under the guise of open-source projects on GitHub, cybercriminals are distributing malware designed to steal users’ personal and financial data. This campaign, dubbed GitVenom, has infiltrated hundreds of repositories and has been operating for no less than two years.
Attackers disguise their malware as automation tools for Instagram, Telegram-based Bitcoin wallet bots, and even a cheat program for Valorant. However, these functionalities are entirely fictitious—instead, users inadvertently infect their devices with malicious code that exfiltrates sensitive data and alters cryptocurrency wallet addresses copied to the clipboard.
According to researchers from Kaspersky Lab, the attackers have already stolen at least 5 Bitcoins, equivalent to $456,600 at the time of publication. The primary victims of the attack have been recorded in Russia, Brazil, and Turkey.
The malicious code is written in various programming languages, including Python, JavaScript, C, C++, and C#. Regardless of the language, the objective remains the same—to download and execute additional malware from attacker-controlled GitHub repositories. Among the most dangerous modules is an infostealer built on Node.js, capable of harvesting passwords, banking details, saved accounts, and browser history, before transmitting the stolen information to the attackers’ Telegram channels.
Additionally, researchers have identified the use of remote administration tools (RATs) such as AsyncRAT and Quasar RAT, which grant attackers full control over compromised devices. Furthermore, many of the infected repositories contain a clipper malware, a program that automatically replaces copied wallet addresses with those belonging to cybercriminals, thereby redirecting funds into their accounts.
Experts emphasize that attackers are leveraging trusted platforms like GitHub to disseminate malware under the guise of legitimate software. Users are strongly advised to exercise extreme caution when downloading code from open repositories, thoroughly verifying its operations before execution.
Meanwhile, researchers from Bitdefender have uncovered a separate scam targeting esports tournament participants. Cybercriminals compromise YouTube accounts and impersonate professional players such as s1mple, NiKo, and donk, luring Counter-Strike 2 fans into fraudulent skin giveaways. As a result, victims lose access to their Steam accounts, cryptocurrency assets, and valuable in-game items.


