In 2024, while the prevalence of malware and phishing attacks has declined, social engineering tactics have grown increasingly sophisticated. According to a recent CrowdStrike report, cybercriminals are increasingly exploiting legitimate user credentials, circumventing the need for traditional malware.
Phishing is gradually being replaced by more insidious techniques, such as vishing (voice phishing), callback phishing, and IT support impersonation. Threat actors capitalize on trust, coercing victims into willingly surrendering sensitive data while also leveraging legitimate remote administration tools to infiltrate systems undetected.
Generative AI has emerged as a powerful weapon in the cybercriminal arsenal. In 2024, threat actors have harnessed AI models to craft fraudulent LinkedIn profiles, impersonate voices and video footage, disseminate disinformation, develop malicious code, and even generate exploits. Some adversarial groups have reportedly attempted to gain unauthorized access to AI models hosted on platforms such as Amazon Bedrock.
Cyberespionage has also intensified. The number of operations linked to Chinese-affiliated threat groups has surged by 150%, with certain industries experiencing an increase of up to 300%. Key targets include the financial sector, media organizations, manufacturing, and engineering firms. Meanwhile, North Korean hackers have focused on fraud schemes involving the impersonation of IT professionals to infiltrate companies.
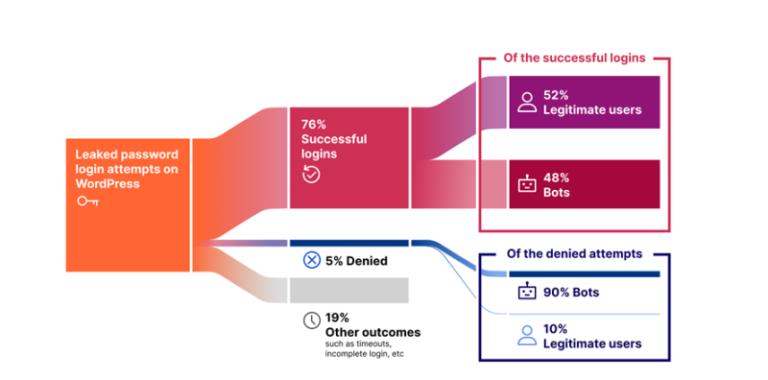
A staggering 79% of cyberattacks in 2024 were carried out without deploying malware. Instead, adversaries relied on stolen credentials and compromised legitimate accounts. The cloud infrastructure proved particularly vulnerable, with 35% of cloud breaches originating from account compromise. Interactive credential hijacking has become a common attack vector, where cybercriminals, masquerading as IT support agents or financial operators, manipulate victims into granting access.
To counter the growing threat of social engineering, CrowdStrike recommends:
- Implementing video verification for password resets to prevent unauthorized account takeovers.
- Training IT support teams to recognize and respond to suspicious requests.
- Adopting phishing-resistant authentication methods, such as FIDO2.
- Monitoring MFA implementations, ensuring that a single phone number is not used across multiple accounts.
The rise in cybercrime is closely tied to the expansion of underground cybercriminal ecosystems. In 2024, the number of access brokers selling compromised credentials surged by 50%, allowing threat actors to focus on more sophisticated attacks without engaging in initial breaches.
To fortify defenses against emerging threats, organizations must deploy advanced threat detection systems, enforce phishing-resistant multi-factor authentication (MFA), and strengthen cloud security measures. Regular software updates and timely patching remain foundational pillars of cyber resilience.