Image: Unit 42
Hudson Rock has introduced BlackBastaGPT—an advanced chatbot trained on over one million leaked internal messages from the Black Basta cybercriminal group. This tool enables researchers to analyze the gang’s operations, financial strategies, and attack methodologies using natural language queries.
The initiative follows a major data leak on February 11, 2025, which exposed chat records containing 367 unique links to targeted organizations, cryptocurrency wallets, phishing templates, and candid discussions among group members.
The leak was published by a user known as ExploitWhispers, who claimed to have acted in retaliation for Black Basta’s cyberattacks on Russian banks. The leaked materials unveiled internal conflicts, identified key figures within the gang, and shed light on their operational structure. Notably, among those implicated were the suspected leader Oleg Nefyodov (alias “Trump”), administrator YY, and even a 17-year-old hacker.
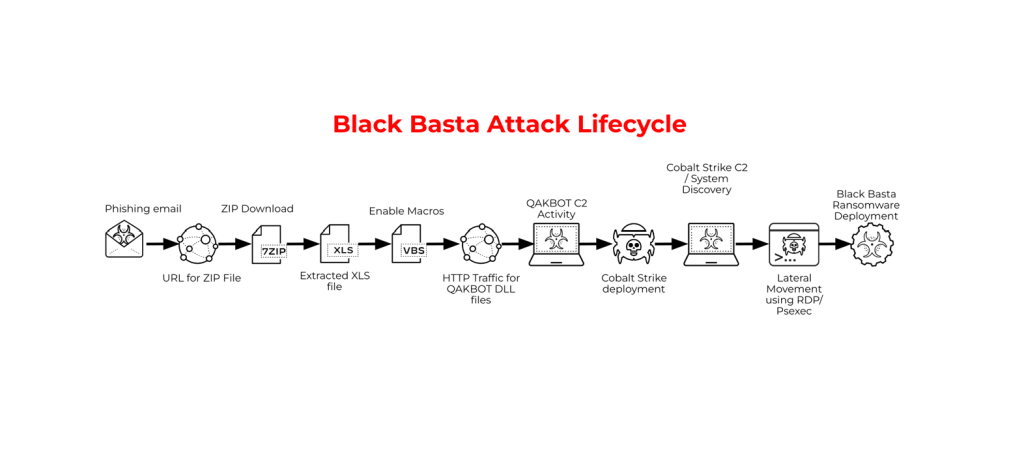
Additionally, the leak provided insights into the vulnerabilities that Black Basta actively exploited. These included security flaws in Citrix, Ivanti, and Fortinet products, as well as phishing campaigns impersonating IT support services to distribute Cobalt Strike and SystemBC malware.
The BlackBastaGPT chatbot is capable of processing vast amounts of data, allowing researchers to craft complex queries. For example, users can identify the gang’s initial access vectors or analyze how ransom amounts were calculated.
According to chat logs, Black Basta leveraged ZoomInfo data to assess victims’ annual revenues, tailoring ransom demands based on their financial standing. Further analysis revealed money laundering schemes, profit distribution disputes, and details of attacks involving Qakbot, Cobalt Strike, and a newly adopted tool, Brute Ratel.
Beyond technical intelligence, the leak also contained sarcastic remarks from gang members, who mocked media coverage of their cyberattacks. Investigators were able to pinpoint the group’s priority targets, which included healthcare and financial organizations.
The leaked data corroborates warnings from the FBI and CISA, confirming that Black Basta has been responsible for over 500 cyberattacks, with cumulative damages exceeding $100 million. Key findings from the breach include:
- The group exploited vulnerable VPNs, RDP servers, and ESXi hosts, using intelligence gathered from over 380 ZoomInfo links.
- In addition to conventional tools like Cobalt Strike, Black Basta experimented with novel evasion techniques.
- Internal discussions exposed Bitcoin laundering operations and financial disputes among members.
Cybersecurity analysts at PRODAFT warn that other criminal groups may adopt Black Basta’s tactics and techniques, now publicly available. Organizations are advised to tighten remote access controls, enforce multi-factor authentication (MFA), and monitor Indicators of Compromise (IOCs), including the use of malicious executables like “AntispamConnectUS.exe”.
The introduction of BlackBastaGPT marks a paradigm shift in cyber threat intelligence, allowing security professionals to proactively predict and counteract cyber threats rather than merely responding to attacks. By studying adversaries from within, defenders can transform criminal intelligence into an effective strategy for cyber defense.