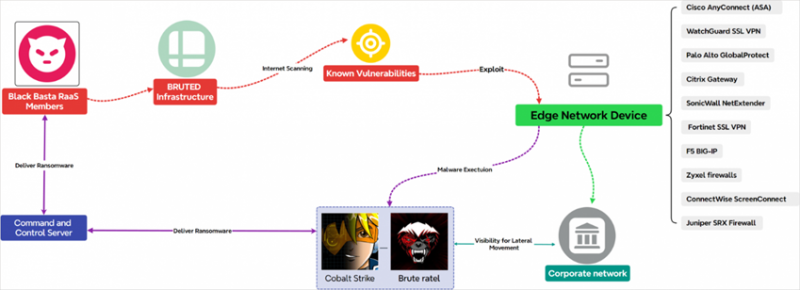
The Black Basta cybercriminal group has introduced a new tool for breaching network devices, known as BRUTED. This sophisticated framework automates brute-force attacks against internet-exposed systems, including firewalls and VPNs, enabling adversaries to scale their operations with minimal effort.
According to EclecticIQ, Black Basta has been leveraging BRUTED since 2023 to conduct automated intrusions into remote access systems. The tool specifically targets credential stuffing against services such as SonicWall NetExtender, Palo Alto GlobalProtect, Cisco AnyConnect, Fortinet SSL VPN, Citrix NetScaler, Microsoft RDWeb, and WatchGuard SSL VPN.
BRUTED scans the internet for vulnerable devices by analyzing public domains and IP addresses before transmitting identified targets to a command-and-control (C2) server. The system then executes high-speed, multi-threaded authentication attacks using password databases sourced from external leaks combined with locally generated variations.
Additionally, the framework analyzes SSL certificates from targeted devices, extracting domain names and other metadata to generate further password permutations. To obfuscate its infrastructure, Black Basta utilizes a proxy network that masks domain names, making detection and attribution more challenging.
Automated password-cracking frameworks like BRUTED pose a significant threat to corporate networks. To mitigate these risks, security experts recommend the following measures:
- Employ complex and unique passwords for all VPN accounts and perimeter network devices.
- Enforce multi-factor authentication (MFA) to prevent unauthorized access, even in cases of credential compromise.
- Monitor for anomalous login attempts, including excessive failed authentications and access attempts from unfamiliar locations.
- Implement login rate limits and account lockout mechanisms to disrupt brute-force attempts.
- Regularly update network device firmware, even if the tool relies solely on credential stuffing rather than exploiting vulnerabilities.
EclecticIQ has released a list of IP addresses and domains associated with BRUTED, which can be used to configure firewall rules and block known malicious entities.
In February, an anonymous informant leaked an archive of Black Basta’s internal chats online. It remains unclear whether ExploitWhispers—the individual responsible for the leak—is a cybersecurity researcher who gained access to the group’s infrastructure or a disgruntled former affiliate exposing insider information. Preliminary assessments suggest the breach may have resulted from internal conflicts within the cybercriminal organization.