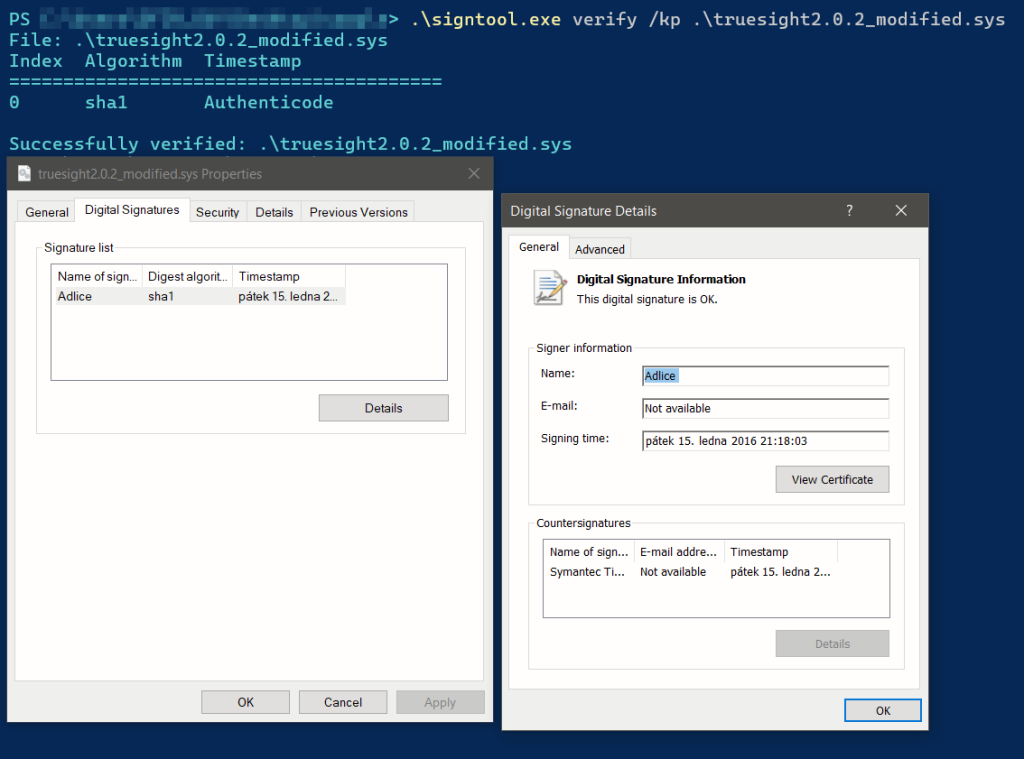
Modified variant of the legacy Truesight driver – valid signed. | Source: Check Point
Cybercriminals are actively exploiting a vulnerable Windows driver from Adlice’s security products to bypass protective mechanisms and propagate the Gh0st RAT malware. According to Check Point, attackers have modified segments of the executable file in version 2.0.2 of the driver while retaining its digital signature, effectively evading detection methods.
Experts have identified thousands of malicious samples leveraging the Bring Your Own Vulnerable Driver (BYOVD) technique to disable security software. VirusTotal has already recorded over 2,500 instances of the compromised version 2.0.2 of the RogueKiller Antirootkit driver (truesight.sys), though the actual number is likely significantly higher. The first known sample, designed to terminate Endpoint Detection and Response (EDR) systems, was discovered in June 2024.
The driver vulnerability, which allows for arbitrary process termination, affects all versions below 3.4.0. This flaw was previously weaponized in Darkside and TrueSightKiller proof-of-concept exploits, which became publicly available in November 2023. By March 2024, SonicWall observed the driver being integrated into the DBatLoader dropper, which disabled security measures prior to deploying Remcos RAT.
Several indicators suggest that this malware campaign may be linked to the Silver Fox group, as evidenced by similar attack techniques, infection vectors, and unique characteristics in the malicious code’s implementation. Approximately 75% of victims are located in China, with additional infections reported in Singapore and Taiwan.
The malware is disseminated via fraudulent websites advertising discounts on luxury goods, as well as through scam channels on messaging platforms such as Telegram. The initial infection stage involves malware masquerading as legitimate applications, which then download the vulnerable driver alongside an additional payload disguised as a PNG, JPG, or GIF file.
In the second phase of the attack, an additional malware strain is retrieved, which subsequently activates the EDR-killer module before deploying Gh0st RAT.
Check Point highlights that malicious versions of the Truesight driver can be deployed not only in the initial infection stage but also by the security-disabling module itself if the driver is not already present on the system. This reinforces the notion that the EDR-killer component is an integral part of the attack chain, yet remains capable of operating independently.
The attackers utilized the BYOVD technique to terminate antivirus and EDR processes, circumventing Windows’ built-in driver blocklisting mechanisms. The final stage of the attack involves deploying a modified version of HiddenGh0st, which enables remote control over compromised systems, espionage, and data exfiltration.
Microsoft added the driver to its blocklist on December 17, 2024, effectively preventing further exploitation. However, Check Point’s analysis suggests that attackers have manipulated the executable’s structure, allowing them to circumvent even the latest security measures, including Microsoft’s Vulnerable Driver Blocklist.


