A critical vulnerability has been identified in MegaRAC Baseboard Management Controller (BMC) software, developed by American Megatrends International (AMI), enabling attackers to seize control over servers and potentially render them inoperable.
MegaRAC BMC is a remote server management platform that enables administrators to oversee hardware without physical access. This technology is widely utilized across server products from over ten major vendors, including HPE, Asus, ASRock, and various other providers catering to cloud infrastructures and data centers.
This security flaw, rated at the highest severity (CVSS score of 10/10) and designated as CVE-2024-54085, can be exploited remotely without authentication or complex intervention. According to security researchers at Eclypsium, the vulnerability originates in the Redfish remote management mechanism and internal interfaces interacting with the BMC.
Successful exploitation grants attackers full dominion over the server—allowing them to deploy malware, alter firmware, initiate endless reboot loops, and, in severe instances, irreparably damage motherboard components (including BMC, BIOS/UEFI) or incapacitate servers entirely via deliberate voltage overloads.
Experts at Eclypsium uncovered this issue while analyzing patches AMI released for CVE-2023-34329, another authentication flaw disclosed in July 2023. Confirmed vulnerable devices include the HPE Cray XD670, Asus RS720A-E11-RS24U, and ASRockRack servers, though it is presumed numerous additional models and vendors are also affected.
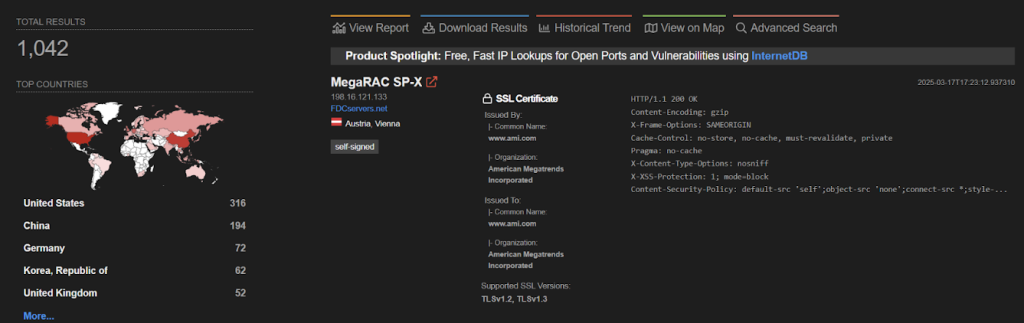
According to Shodan data, over 1,000 vulnerable servers remain publicly accessible online, thereby exposing them to potential exploitation. CVE-2024-54085 is not an isolated issue; since 2022, Eclypsium has documented multiple severe vulnerabilities within MegaRAC BMC, including CVE-2022-40259, CVE-2022-40242, CVE-2022-2827, CVE-2022-26872, and CVE-2022-40258, all capable of enabling unauthorized control, firmware tampering, and malware distribution.
Moreover, in July 2023, researchers identified yet another critical flaw, CVE-2023-34330, involving code injection via the Redfish interface. Additionally, CVE-2022-40258—relating to weak password hashing—renders compromising administrative BMC accounts alarmingly straightforward.
Although there have been no confirmed real-world attacks exploiting CVE-2024-54085 to date, security analysts warn that developing an exploit remains relatively simple, given the lack of encryption in firmware binaries.
Security professionals strongly advise immediate application of updates released on March 11 by AMI, Lenovo, and HPE, recommend disabling direct internet access to MegaRAC BMC interfaces, and urge meticulous monitoring of server logs for suspicious activity.
Eclypsium emphasizes that while this vulnerability specifically impacts AMI’s BMC software stack, its widespread adoption across numerous hardware vendors amplifies the potential damage significantly. Given that patching involves temporary server downtime, the remediation process may pose operational challenges, yet delaying it could prove critically perilous.