Source: ESET
Freelance software developers have become the latest targets of a sophisticated cyberattack campaign distributing the malware strains BeaverTail and InvisibleFerret. This operation, dubbed DeceptiveDevelopment, has been linked to North Korean hackers and is believed to have commenced around 2023.
The attackers’ primary objective is to gain unauthorized access to victims’ cryptocurrency wallets and account credentials. To achieve this, they employ social engineering tactics, creating fraudulent recruiter profiles and reaching out to developers on specialized job-seeking platforms. Victims are then sent malicious code disguised as a task within a supposed job interview process.
The targeted platforms include GitHub, GitLab, Bitbucket, Upwork, Freelancer.com, We Work Remotely, Moonlight, and Crypto Jobs List. Victims are often asked to debug code or add new functionality to a cryptocurrency-related project, which, unbeknownst to them, contains embedded malicious code. This code is frequently concealed within an innocuous-looking fragment, making detection particularly challenging.
In some instances, the attackers persuade victims to install counterfeit video conferencing applications, such as MiroTalk or FreeConference, which have been laced with malware. Once installed, the infection process begins, initiating the exfiltration of sensitive data.
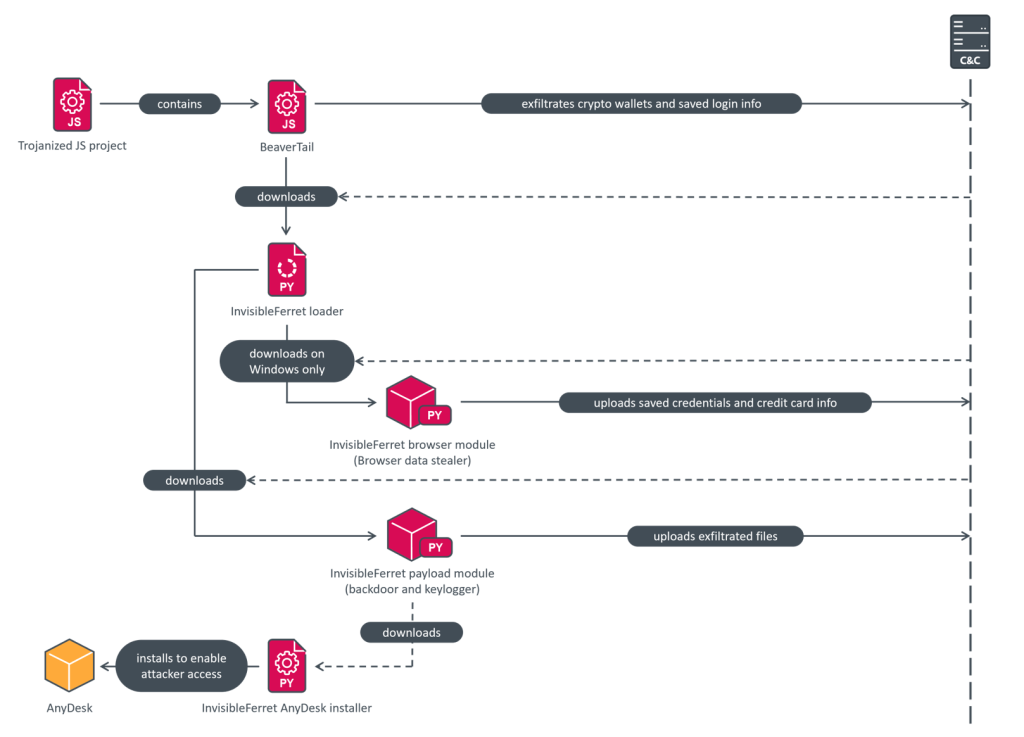
BeaverTail functions as a loader for InvisibleFerret and exists in two distinct versions: one written in JavaScript, which is embedded into projects, and another built using the Qt framework, masquerading as video conferencing software.
InvisibleFerret is a modular Python-based malware composed of three core components. The first module (“pay”) collects system information, logs keystrokes, intercepts clipboard data, executes attacker-sent commands, and exfiltrates files. The second module (“bow”) specializes in credential theft, extracting saved passwords and autofill data from browsers including Chrome, Brave, Opera, Yandex, and Edge. The third module (“adc”) ensures persistent access by installing AnyDesk, granting attackers remote control over the infected machine.
According to ESET, the attack campaign has targeted cryptocurrency developers across multiple countries, including Finland, India, Italy, Pakistan, Spain, South Africa, Russia, Ukraine, and the United States. The attackers appear to be opportunistic, aiming to compromise as many systems as possible, regardless of geographic location.
Security researchers have noted that the attackers exhibit a relatively low level of coding sophistication—their malware contains developer comments, hardcoded test IP addresses, and other indicators of rushed execution. However, their tactics are rapidly evolving, growing more refined and deceptive over time.
The use of fake job interviews as a lure is not new to North Korean hacking groups. A similar technique was previously observed in Operation Dream Job. Additionally, there is substantial evidence suggesting that North Korean operatives engage in fraudulent employment schemes, using false identities to secure IT jobs abroad, ultimately funneling earnings back to the regime.
ESET emphasizes that DeceptiveDevelopment is part of a broader North Korean cyber strategy aimed at stealing cryptocurrency assets. As these threat actors refine their toolsets, their malware deployment techniques become increasingly sophisticated and difficult to detect.


