A new and highly dangerous ransomware variant, DragonForce, has been detected in the wild, exhibiting the capability to encrypt files on compromised systems and demand ransom payments in cryptocurrency. This malware propagates through phishing attacks, malicious websites, and the exploitation of vulnerabilities, all while adeptly masquerading as legitimate files.
According to experts at Resecurity, once infiltrated, DragonForce employs multiple persistence techniques, including self-replication across directories, modification of the Windows registry, and the creation of scheduled tasks to ensure automatic execution upon system reboot. The ransomware further conceals its presence by erasing system logs and disabling antivirus programs.
To escalate privileges, attackers leverage token manipulation techniques and execute processes under administrator credentials. The malicious code is heavily encrypted and employs DLL side-loading with obfuscated function names, significantly complicating detection. Analysts have identified text-based signatures in Chinese within the code, suggesting the potential international origins of the threat.
The primary objective of DragonForce is to encrypt user data using AES-256 and RSA encryption algorithms. Upon execution, affected files are assigned a new extension: “.dragonforce_encrypted”, with the unique decryption key retained exclusively by the attackers. Additionally, the malware gathers extensive system information—including OS version, installed applications, and network configurations—logging these details in a file stored at C:\Users\Public\log.log.
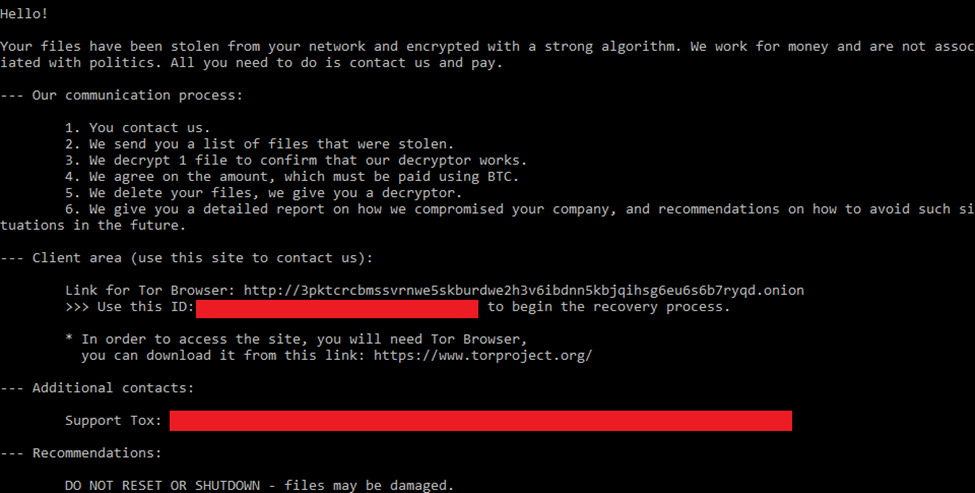
Like other modern ransomware strains, DragonForce leaves behind a ransom note in the form of a README.txt file, placed on the desktop and within affected directories, detailing payment instructions. Victims are directed to an anonymous darknet site, where they are coerced into making ransom payments in Bitcoin.
For lateral movement within a network, the malware exploits RDP and SMB protocol vulnerabilities, in addition to utilizing stolen credentials to target other connected devices. Analysts have linked one of the command-and-control (C2) servers to Iran, though the presence of Chinese code signatures hints at potential collaboration between international hacker groups.
Cybersecurity specialists strongly advise organizations and users to maintain regular system updates, monitor network traffic, and implement robust data backup policies. Network activity surveillance, the use of reliable endpoint protection solutions, and strict security policies can significantly mitigate the risk posed by such sophisticated ransomware threats.


