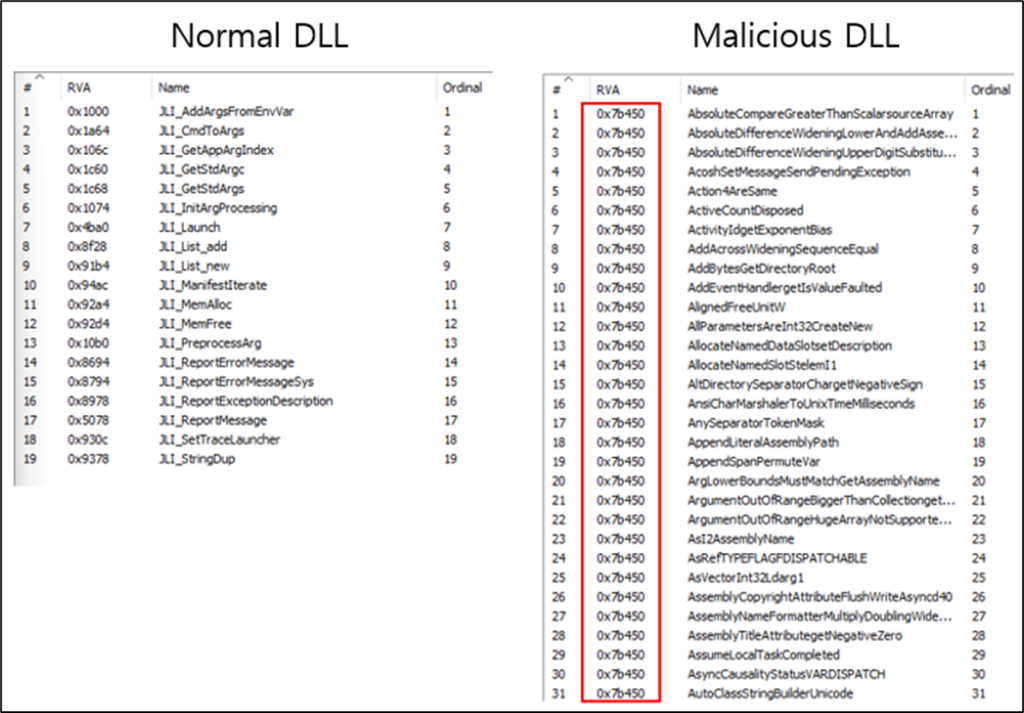
Comparison of export function lists: legitimate jli.dll vs. malicious jli.dll
Cybercriminals continue to refine their techniques for concealing malicious software, leveraging legitimate programs to circumvent security mechanisms. One such method, DLL Sideloading, enables the execution of malicious libraries through trusted applications.
Recently, researchers at the AhnLab Security Intelligence Center (ASEC) uncovered a new campaign distributing the infostealer XLoader, in which threat actors exploit the jarsigner utility, a component of the Eclipse IDE.
The attack begins with the dissemination of a compromised ZIP archive containing three files: a renamed jarsigner.exe (disguised as Documents2012.exe), a counterfeit jli.dll that loads the malicious concrt140e.dll, and the XLoader dropper itself. When Documents2012.exe is executed, it triggers the tampered jli.dll, ultimately leading to the deployment of XLoader.
Once successfully executed, the malicious code is injected into the legitimate aspnet_wp.exe process, effectively obfuscating XLoader’s presence within the system. The malware’s primary objective is to exfiltrate confidential data, including browser credentials and user account information. Additionally, XLoader has the capability to download and execute supplementary malicious payloads.
XLoader is a direct successor to the notorious Formbook malware and operates under the Malware-as-a-Service (MaaS) model. First identified in 2020, it has continuously evolved, with a macOS variant discovered in 2023 masquerading as Microsoft Office. The latest iterations of the loader feature advanced evasion techniques, including code encryption and anti-detection mechanisms.
Notably, XLoader employs decoy domain lists to obscure its network traffic, blending real command-and-control (C2) communication with legitimate web requests. This obfuscation strategy has previously been observed in other threats such as Pushdo and SmokeLoader.
Beyond XLoader, researchers have identified new malware loaders—NodeLoader and RiseLoader—which distribute a range of threats, including Vidar, Lumma, Phemedrone, XMRig, and Socks5Systemz. Analysis of RiseLoader suggests a strong code resemblance to another malware strain, RisePro, indicating potential affiliations between cybercriminal groups.
The ongoing evolution of XLoader and other adversarial tools underscores the increasing sophistication of cyberattacks and the widespread adoption of stealth techniques. Both individuals and organizations must remain vigilant by ensuring their security solutions are regularly updated and exercising caution when handling files from untrusted sources.


