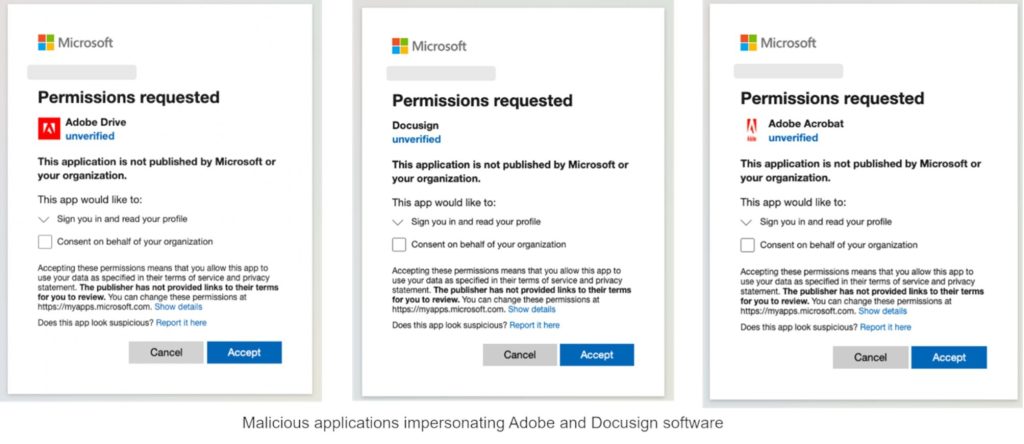
Researchers from Proofpoint have identified a sophisticated cyber campaign wherein attackers are propagating malicious OAuth applications by masquerading them as legitimate Adobe and DocuSign services. Their primary intent is to steal Microsoft 365 credentials and disseminate malware.
This campaign hinges upon fraudulent applications deceptively named Adobe Drive, Adobe Drive X, Adobe Acrobat, and DocuSign. These apps request a minimal range of permissions—profile access, email address visibility, and the OpenID identifier—which strategically minimizes user suspicion.
Once permissions are granted, the perpetrators gain access to the user’s name, unique username, primary email address, profile image, and primary account details. Subsequently, this personal information can facilitate targeted cyberattacks or sophisticated social engineering schemes.
Phishing campaigns were executed via compromised accounts belonging predominantly to small enterprises and charitable organizations, with phishing emails meticulously crafted to masquerade as legitimate correspondence. These compromised accounts were primarily associated with small businesses and nonprofits operating in charitable sectors within communities. Malicious communications were specifically engineered to entice victims with phishing links camouflaged as legitimate Microsoft 365 login pages or directly prompt malware downloads.
After a user authorizes the malicious OAuth application, they are redirected either to fraudulent Microsoft 365 login portals or are immediately presented with malware payloads. Proofpoint’s research revealed that attackers initiated malicious activity immediately following the victim’s authorization.
This phishing strategy mirrors recent incidents where adversaries leveraged OAuth applications to breach GitHub developer accounts and infiltrated third-party platforms to execute ClickFix attacks against automotive dealership clients. In both scenarios, attackers exploited compromised trust to perpetrate secondary malicious activities.
To mitigate such risks, Proofpoint recommends exercising caution by thoroughly scrutinizing requested OAuth permissions and refraining from approving access to unrecognized applications. Users should routinely audit previously authorized applications via Microsoft’s “My Apps” portal (myapplications.microsoft.com) and promptly revoke permissions from suspicious entities. Microsoft 365 administrators are encouraged to restrict end-users’ ability to independently authorize OAuth access, thereby reducing the attack surface.