Cybersecurity researchers have uncovered an unusual malicious Python script in cyberspace that employs an unconventional and rather amusing technique to evade analysis—by simulating the infamous “Blue Screen of Death” (BSOD). This method not only complicates malware analysis but also has the potential to mislead users.
The script exhibits low detectability by antivirus software; on VirusTotal, only 4 out of 59 security solutions identified it. Cybersecurity specialists took notice of it due to its inventive use of Python’s standard Tkinter library, which is typically employed for developing graphical user interfaces.
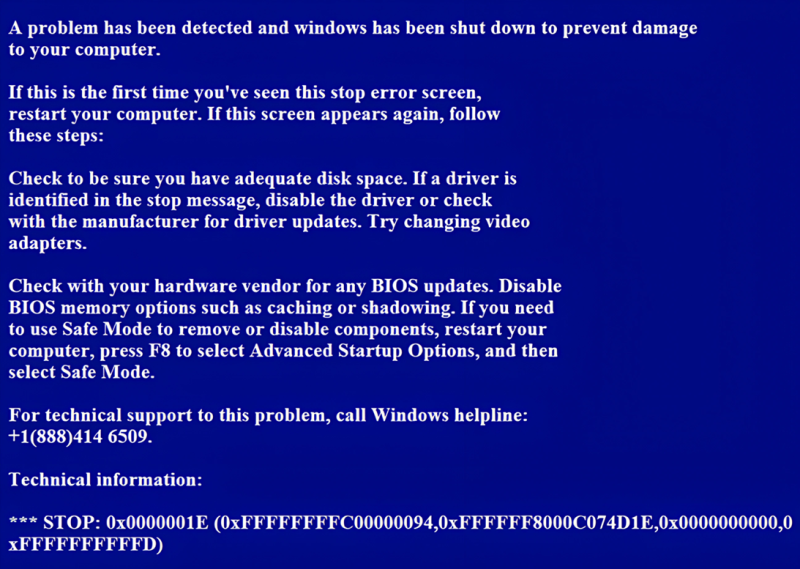
Unlike most Python-based malware, which operates via the command line, this script generates a full-screen window mimicking a BSOD. Created using Tkinter, the window lacks standard control buttons and overlays all other applications, creating the illusion of a critical system failure. The code responsible for this deceptive effect is structured as follows:
root = tk.Tk()
root.configure(background=”dark blue”)
ex = Example(root)
w, h = root.winfo_screenwidth(),
root.winfo_screenheight()
root.overrideredirect(1)
root.geometry(“%dx%d+0+0” % (w, h))
root.wm_attributes(“-topmost”, 1)
root.mainloop()
The on-screen message replicates classic Windows system failure notifications: “A problem has been detected, and Windows has been shut down to prevent damage to your computer.”
Despite its simplicity, this technique is capable of disorienting users and even distracting analysts during malware investigations. The initial reaction of a researcher encountering such a screen might be to simply restart the virtual machine, inadvertently delaying further analysis.
Upon examination, the script was found to lack any severely destructive payload. However, such deceptive tactics can complicate forensic investigations and reverse engineering efforts. A representative from the SANS Institute remarked that while this approach is not revolutionary, its combination with other evasion techniques could enhance the resilience of malicious code.
A particularly concerning aspect is the script’s low detection rate among antivirus solutions, underscoring the necessity of employing behavioral analysis and activity monitoring alongside traditional security mechanisms.
This incident serves as a reminder that even seemingly innocuous “pranks,” such as a fake BSOD, can be integrated into more sophisticated cybercriminal schemes, deceiving both users and security analysts alike.


