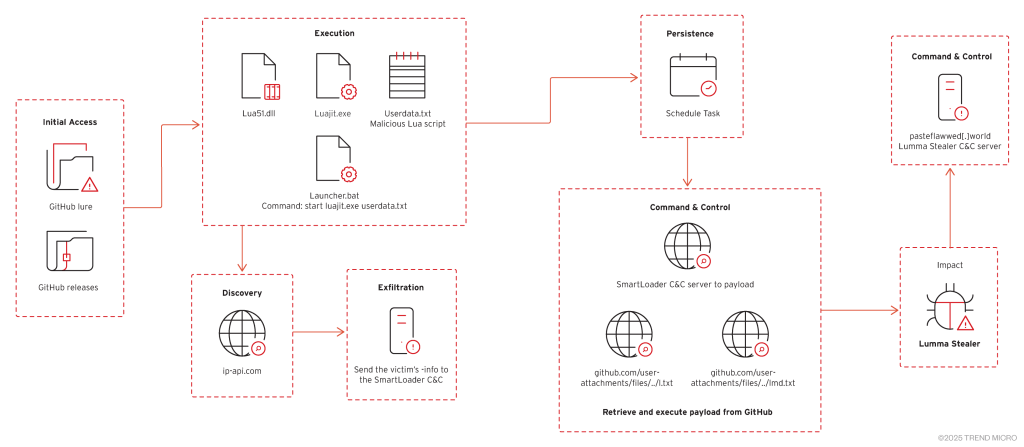
Researchers at Trend Micro have uncovered a malware campaign in which threat actors exploit fraudulent GitHub repositories to distribute malicious software. Disguised as gaming cheats, cracked software, and utility tools, these repositories serve as a delivery mechanism for SmartLoader, which subsequently deploys Lumma Stealer and other malware threats.
The attackers leverage generative AI to create convincing repository descriptions that closely resemble legitimate projects. Within the ZIP archives, they conceal obfuscated Lua scripts, which trigger the execution of malicious payloads upon extraction.
Once infiltrated, Lumma Stealer exfiltrates cryptocurrency wallets, two-factor authentication (2FA) extensions, credentials, and personal data, potentially leading to significant financial losses. While cybercriminals previously uploaded malicious files as attachments on GitHub, they have now shifted to constructing entire deceptive repositories, making detection and takedown efforts considerably more challenging.
Malicious Files Contained in the Infected Archives
- lua51.dll – LuaJIT interpreter library
- luajit.exe – Executable loader for Lua scripts
- userdata.txt – Concealed malicious script
- Launcher.bat – Script for executing luajit.exe
Upon execution, SmartLoader downloads “search.exe,” which activates Lumma Stealer. The infected system then establishes communication with a command-and-control (C2) server at “pasteflawwed[.]world,” transmitting stolen data to the attackers.
Exploiting Trust in GitHub & AI-Driven Automation
Cybercriminals are taking advantage of GitHub’s reputation as a trusted platform to propagate malware. By employing AI-driven automation, they streamline the creation of deceptive repositories, increasing the scale and sophistication of their campaigns.
Security Recommendations to Mitigate the Threat
To safeguard against this evolving threat, security experts advise the following measures:
- Download software only from official sources, avoiding suspicious repositories.
- Verify the authenticity of repositories by analyzing commit history, author activity, and documentation structure.
- Deploy robust antivirus solutions to detect and block potential threats.
- Conduct thorough analysis of downloaded files before execution.
- Implement network security measures to block access to known malicious repositories.
- Monitor network activity for signs of suspicious connections.
- Restrict the execution of unauthorized scripts and applications.
- Educate employees on social engineering tactics and the risks associated with downloading software from unverified sources.
As cybercriminals continuously evolve their tactics, only a proactive approach to cybersecurity can effectively minimize risks and safeguard sensitive data.


