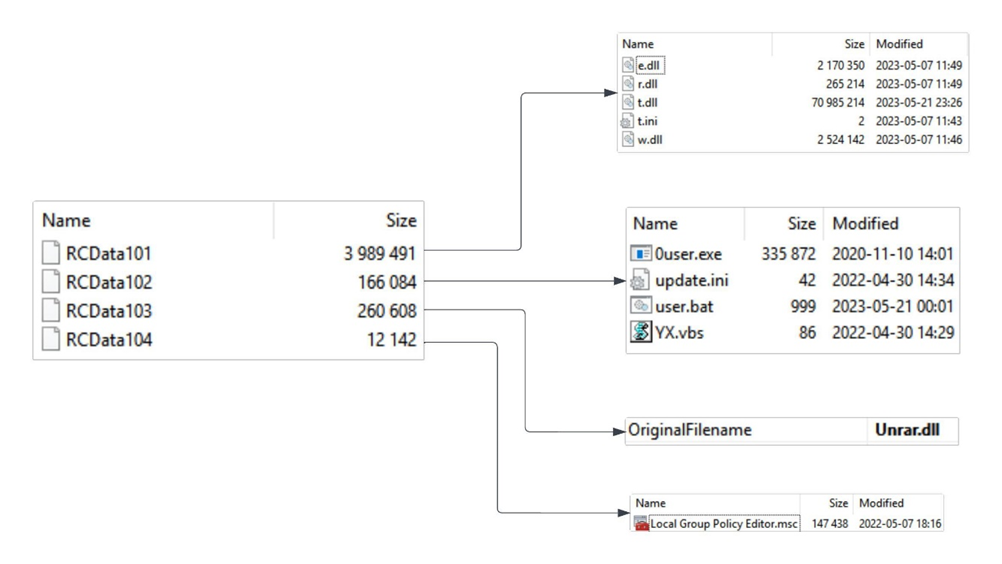
Fangao.dll resource unpacking scheme
Cybercriminals have launched a targeted campaign against industrial organizations in the Asia-Pacific region (APAC), employing sophisticated phishing attacks to disseminate the dangerous FatalRAT malware.
The victims include government institutions and enterprises spanning multiple sectors, including manufacturing, construction, information technology, telecommunications, healthcare, energy, and logistics. The attack has impacted organizations across Taiwan, Malaysia, China, Japan, Thailand, South Korea, Singapore, the Philippines, Vietnam, and Hong Kong.
To execute their campaign, threat actors leveraged Chinese cloud services, including myqcloud and Youdao Cloud Notes, as delivery mechanisms for malicious payloads. According to Kaspersky ICS CERT, the attackers developed a complex, multi-stage infection chain designed to evade security defenses.
The attack begins with a phishing email containing a ZIP archive, named in Chinese characters. Once opened, the first-stage loader is executed, retrieving a DLL library and FatalRAT configuration file from Youdao Cloud Notes. The malware then downloads additional payloads from the cloud service while displaying a decoy file to prevent suspicion.
The primary infection technique revolves around DLL hijacking, allowing the malware to masquerade as legitimate Windows processes. Upon completing the attack sequence, the final-stage payload—FatalRAT—is downloaded from myqcloud[.]com, concealing its presence with a fake error message.
FatalRAT is an advanced remote access trojan equipped with an extensive array of malicious functionalities, including:
- Keystroke logging
- MBR sector manipulation
- Screen monitoring and control
- Exfiltration and deletion of browser data
- Remote software deployment (e.g., AnyDesk and UltraViewer)
- File operations and proxy server management
- Forced termination of system processes
Moreover, FatalRAT employs 17 different anti-analysis techniques to detect virtual environments and sandbox environments, terminating execution if forensic analysis is detected.
Earlier instances of FatalRAT infections were linked to malicious Google Ads campaigns. In September 2023, Proofpoint researchers observed similar attacks distributing Gh0st RAT, Purple Fox, and ValleyRAT. Some of these operations have been attributed to the Silver Fox threat group, which primarily targets Chinese- and Japanese-speaking organizations.
Cybersecurity experts suggest that a Chinese-speaking APT group is responsible for orchestrating these attacks, citing the consistent use of Chinese cloud services and language-based interfaces throughout the infection process.
Experts warn that FatalRAT malware poses a severe security threat, as it grants attackers full control over compromised devices. Organizations are advised to reinforce their defenses against phishing attacks, exercise caution when handling downloads from untrusted sources, and closely monitor network activity for suspicious behavior.


