Source: Elastic Security Labs
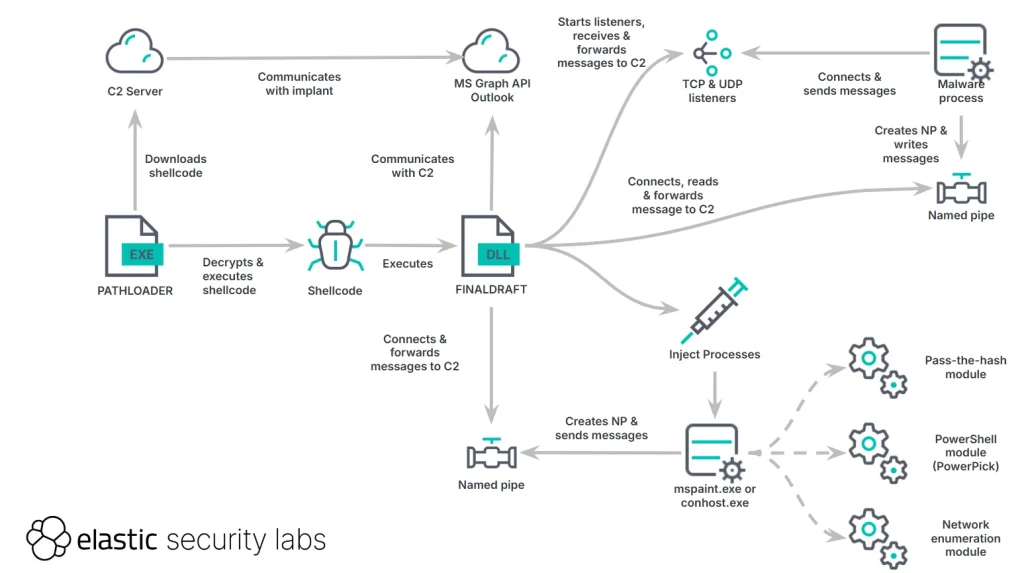
Researchers at Elastic Security Labs have uncovered a sophisticated cyberattack in which threat actors deployed the powerful FINALDRAFT backdoor. The campaign targeted the foreign affairs ministry of a South American nation, as well as a telecommunications company and a university in Southeast Asia.
FINALDRAFT is an advanced remote administration tool, written in C++, capable of loading additional modules, executing arbitrary commands, and leveraging Microsoft Graph API for covert control via drafts in Outlook’s mail service. This stealthy technique was previously observed in another piece of malware—SIESTAGRAPH.
The attackers utilized the certutil utility to download files from a server associated with the foreign affairs ministry. These commands were executed via Windows Remote Management (WinrsHost.exe), indicating that the adversaries had already acquired stolen credentials and gained access to the internal network.
The attack chain was initiated through the PATHLOADER trojan, which retrieved an encrypted shellcode payload before injecting it into the memory of mspaint.exe. This code, once activated, launched FINALDRAFT, granting attackers full control over compromised systems.
The backdoor is highly versatile, supporting 37 distinct commands, including file manipulation, process injection, and network proxy creation. Notably, it is capable of executing commands with stolen NTLM hashes and running PowerShell scripts, effectively bypassing Windows’ built-in security mechanisms. To achieve this, FINALDRAFT integrates PowerPick, a component of the Empire post-exploitation toolkit.
Beyond its Windows variant, researchers also identified a Linux version of FINALDRAFT, uploaded to VirusTotal by users in Brazil and the United States. This iteration maintains a similar feature set, enabling command execution via popen while incorporating mechanisms to conceal its presence.
The analysis suggests that this attack was meticulously orchestrated, with the malware exhibiting a high degree of technical sophistication, indicative of a well-funded and highly skilled development team. However, operational errors and inadequate concealment strategies suggest that the attackers may have been operating under pressure or lacked full control over their campaign.
The prolonged activity of REF7707 and the complexity of its toolset indicate an espionage-driven motive. Against this backdrop, cybersecurity experts underscore the critical need to enhance cyber defenses, particularly within organizations handling sensitive information. They emphasize the importance of continuous threat monitoring and intelligence analysis to preempt and mitigate similar incursions in the future.


