The newly emerged Eleven11bot botnet, reportedly linked to Iran, has compromised more than 86,000 internet-connected devices, primarily IP cameras and network video recorders (NVRs). These infected devices are being leveraged to orchestrate large-scale DDoS attacks targeting telecommunications companies and online gaming servers.
The threat was first identified by Nokia researchers, who subsequently shared their findings with the GreyNoise monitoring platform. According to cybersecurity expert Jérôme Meyer, Eleven11bot represents one of the most significant botnet campaigns in recent years. He noted that even in its early stages, the number of infected devices had surpassed 30,000, and its continued proliferation has made it one of the most expansive attacks launched by non-state-affiliated groups since 2022.
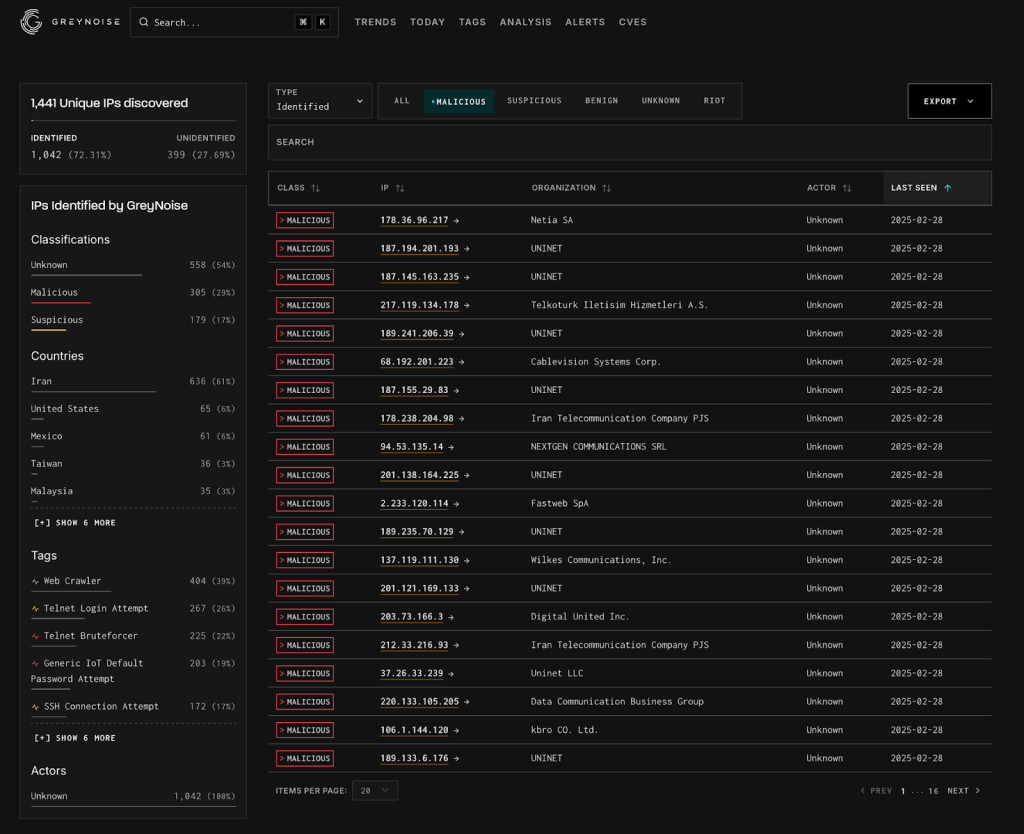
Data from Shadowserver indicates that the number of infected devices has now reached 86,400, with the majority located in the United States, the United Kingdom, Mexico, Canada, and Australia. Traffic analysis has revealed that botnet attacks can generate hundreds of millions of packets per second, with some assaults lasting for several days.
Experts from GreyNoise, in collaboration with Censys, have identified 1,400 IP addresses linked to Eleven11bot activity. In 96% of cases, the infected devices were confirmed to be real rather than spoofed. The highest concentration of malicious IP addresses was found in Iran, with more than 300 of them classified as actively malicious.
The botnet propagates through brute-force attacks, default credentials preinstalled on specific IoT device models, and network scanning for exposed Telnet and SSH ports. GreyNoise has published a list of IP addresses associated with Eleven11bot and recommends that security systems block these addresses while also monitoring for suspicious login attempts.
To mitigate the risk of infection, security experts advise regularly updating IoT firmware, disabling remote access when unnecessary, and replacing default factory passwords with strong, unique credentials. Furthermore, given the limited lifespan of IoT security support, users are encouraged to routinely assess their device status and replace outdated models with modern solutions that incorporate up-to-date security measures.


