A cross-site scripting (XSS) vulnerability in a widely used framework for virtual 360° tours has been exploited by malicious actors to inject harmful scripts into hundreds of websites. The objective of this attack is to manipulate search engine results and orchestrate a large-scale spam advertising campaign.
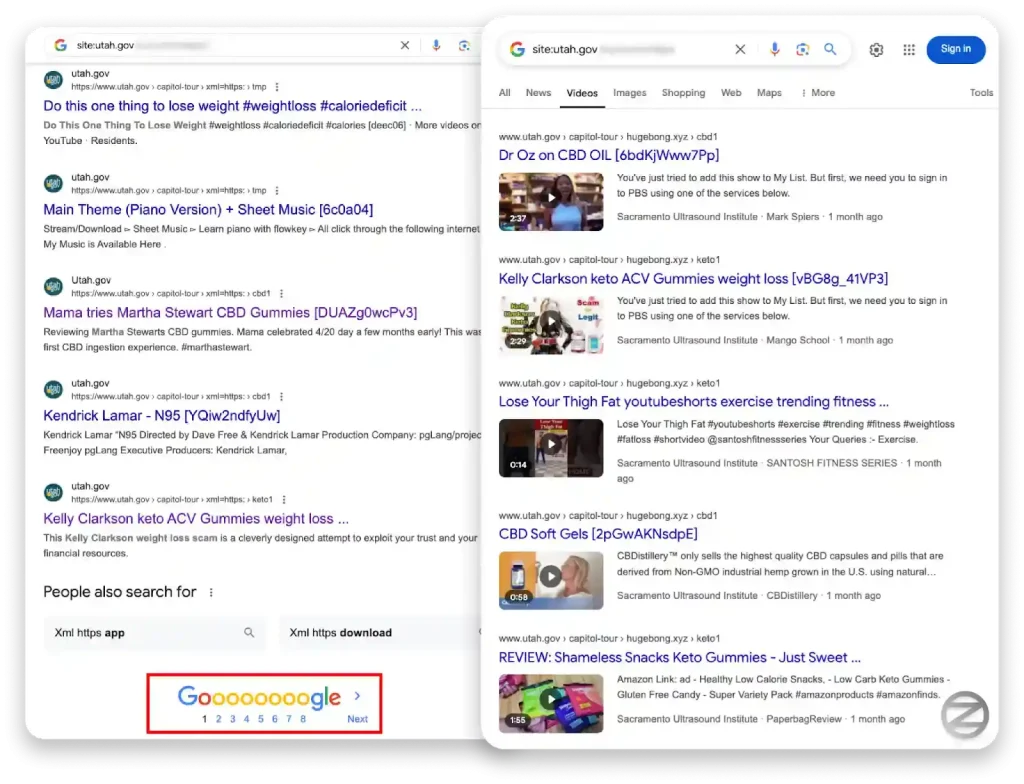
According to independent security researcher Oleg Zaytsev, the campaign—dubbed 360XSS—has compromised over 350 websites, including government portals, universities, hotels, automobile dealerships, and Fortune 500 corporations.
All affected sites utilized Krpano, a popular framework for embedding 360° images and videos to create virtual tours. Zaitsev stumbled upon the campaign by chance when he noticed pornographic content being advertised through a domain belonging to Yale University.
The attack exploits an XML parameter that enables the loading of external configurations. Malicious code, encoded in Base64, is executed upon visiting a crafted URL, leading users to redirected advertising pages. The passQueryParameters function in Krpano processes HTTP parameters, inadvertently exposing the XSS vulnerability.
The issue in Krpano was first documented in 2020 with the registration of CVE-2020-24901, which carried a CVSS score of 6.1. In response, the framework’s developers released version 1.20.10, restricting parameter transmission to an allowlist. However, research has revealed that explicitly adding an XML parameter to the exclusion list inadvertently reintroduces the vulnerability.
According to Zaitsev, attackers leveraged this flaw to hijack trusted domains on a massive scale, using them to promote gambling ads, dietary supplements, fake news, and even artificially boost YouTube views. The use of XSS for SEO poisoning allowed these fraudulent sites to climb search rankings, creating an illusion of legitimacy.
Although XSS typically requires user interaction, in this case, the propagation of malicious links via search engines significantly amplified the attack’s effectiveness. Zaitsev described the technique as highly creative, emphasizing its ability to bypass conventional security measures with ease.
Following the disclosure, Krpano developers released version 1.22.4, which completely disables support for external XML configurations. The passQueryParameters function can no longer reference URLs beyond the current directory.
The identities of the attackers remain unknown, but the nature of the campaign suggests ties to an advertising network employing dubious monetization tactics. Website owners using Krpano are strongly advised to update to the latest version and disable passQueryParameters. Those already affected should locate and remove compromised pages using Google Search Console.


