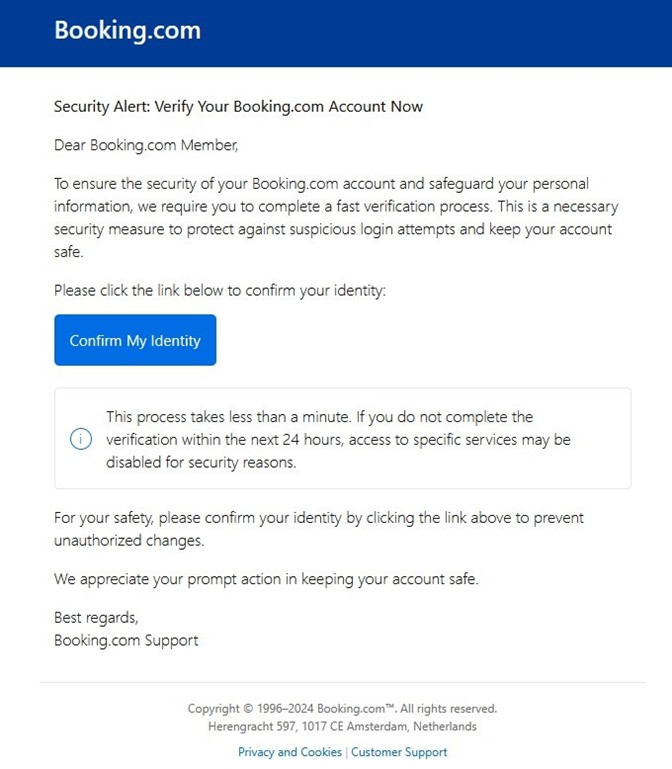
A sample phishing email, purportedly requiring the recipient to verify their Booking.com account.
Since December 2024, on the eve of one of the busiest travel seasons, Microsoft Threat Intelligence has been tracking a widespread phishing campaign impersonating the well-known booking agency Booking.com. The primary targets of this operation are organizations within the hospitality sector. Using the ClickFix social engineering technique, threat actors distribute malware, steal credentials, and engage in financial fraud.
Phishing emails have been sent to hospitality industry employees across North America, Oceania, South and Southeast Asia, and all regions of Europe. The attackers disguise their fraudulent messages as official communications from Booking.com, using a variety of pretexts, including:
- Negative guest reviews
- Reservation requests
- Online promotion offers
- Account verification requests
The defining characteristic of this attack is the use of ClickFix, a method that leverages human instinct to resolve issues immediately. Threat actors create fake error messages or security warnings, coercing victims into entering a command in the Windows “Run” dialog. This command, silently copied to the clipboard, triggers the download and execution of malware via “mshta.exe”. This technique bypasses automated security defenses, as the attack requires direct user interaction to succeed.
Microsoft analysts attribute this activity to a threat actor tracked as Storm-1865. The group employs a diverse array of malware, including:
- XWorm
- Lumma Stealer
- VenomRAT
- AsyncRAT
- Danabot
- NetSupport RAT
These tools are designed to exfiltrate financial data and credentials, aligning with Storm-1865’s previous activities.
In 2023, Storm-1865 used similar techniques to target Booking.com customers, shifting in 2024 to phishing schemes in the e-commerce sector. The adoption of ClickFix represents an evolution in their tactics, demonstrating sophisticated attempts to evade traditional security measures.
To mitigate the risk of phishing attacks, Microsoft recommends that organizations educate employees on identifying fraudulent emails. Key indicators of phishing attempts include:
- Suspicious sender addresses
- Unexpected or urgent requests
- Links leading to fraudulent domains
- Grammar and spelling errors in emails
Verifying URLs before clicking and navigating to services directly via official websites can significantly reduce the risk of compromise.
Organizations should implement multiple layers of security to counter such threats, including:
- Multi-factor authentication (MFA) to prevent unauthorized account access
- Cloud-based antivirus solutions for real-time threat detection
- Blocking potentially dangerous scripts to neutralize attack vectors
- Enabling SmartScreen protection in browsers to filter out malicious sites
- Activating Zero-hour Auto Purge (ZAP) in Office 365 to remove phishing emails after delivery
- Applying strict execution policies for corporate environments to limit code execution risks
For Microsoft Defender XDR users, additional threat detection and mitigation mechanisms are available. Microsoft also advises enabling fully automated investigation and remediation, allowing for instant attack neutralization and reducing the volume of security incidents.
The Storm-1865 phishing campaign underscores the rapid evolution of cyber fraud schemes and the growing necessity for proactive security measures. Organizations within the hospitality industry and beyond must enhance employee awareness of emerging threats and implement comprehensive cybersecurity strategies to prevent network compromise.


