Second part of the compromise chain | Image: ESET
Cyber threat researchers at ESET have unveiled new details regarding the malicious campaign AkaiRyū, orchestrated by the Chinese cyber-espionage group MirrorFace. The attack, detected in late August 2024, targeted a diplomatic institute in Central Europe, with infection lures disguised as documents related to Expo 2025, an international exhibition set to commence soon in Osaka, Japan.
MirrorFace, also known as Earth Kasha, has been active since at least 2019 and is considered a subset of the broader APT10 group. While its operations have traditionally focused on Japanese organizations, this latest campaign marks a notable expansion in its geographic scope.
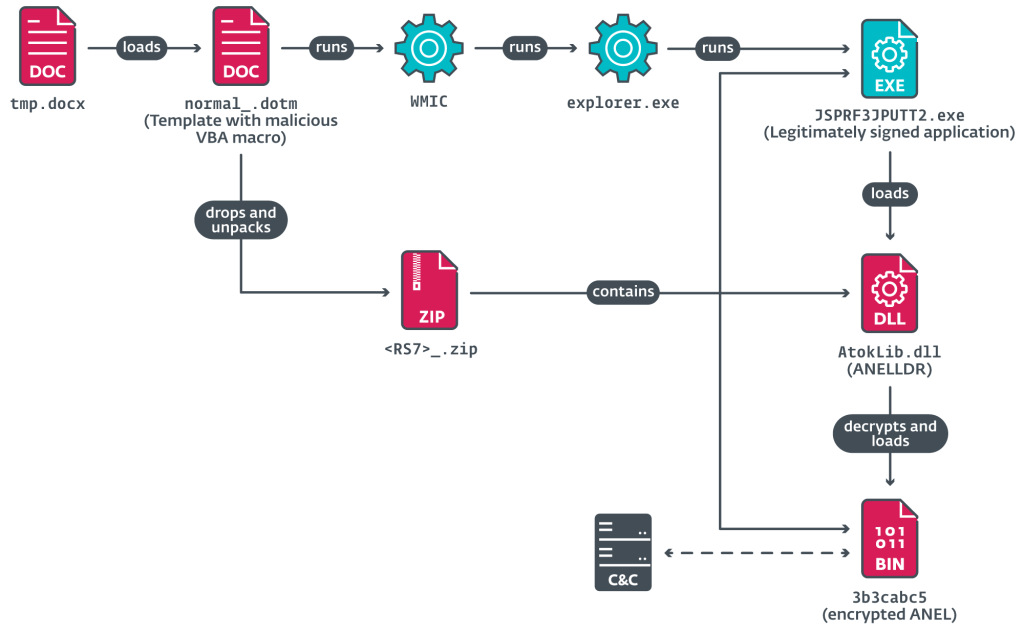
In this attack, the threat actors deployed a modified version of the AsyncRAT remote access Trojan alongside the ANEL (also known as UPPERCUT) backdoor, a tool previously linked to APT10. This shift is significant, as the group had historically relied on LODEINFO but has now transitioned to ANEL. The last recorded instance of ANEL usage dates back to 2018–2019, after which it was presumed abandoned.
ESET researchers have yet to determine why MirrorFace has replaced LODEINFO with ANEL. However, LODEINFO has not been observed in attacks since early 2024, suggesting that the group may have made a definitive transition to new tooling.
Experts also noted that Operation AkaiRyū overlaps with Campaign C, previously documented by Japanese law enforcement and the National Cyber Security Center (NCSC) in January 2025. Among the newly identified tactics is the use of a modified AsyncRAT variant in combination with Visual Studio Code Remote Tunnels, a service leveraged for stealthy remote access to compromised systems. This technique has gained popularity among Chinese cyber-espionage groups in recent months.
The primary infection vector remains phishing emails embedded with malicious documents or links. Upon execution, the downloaded component ANELLDR initiates a DLL Sideloading mechanism, decrypting and launching ANEL. Additionally, the attackers deployed a modular backdoor, HiddenFace (also known as NOOPDOOR), an exclusive tool used by MirrorFace.
Despite these findings, ESET specialists acknowledge that significant gaps remain in fully mapping the attack chain. One key challenge lies in MirrorFace’s heightened operational security measures. The group systematically removes deployed tools and files, erases Windows event logs, and executes malware within Windows Sandbox environments, significantly complicating forensic analysis.
Cyberattacks like AkaiRyū serve as a stark reminder that adversaries continuously evolve—adapting their tools, tactics, and attack geographies to evade detection. This underscores the critical need for continuous cybersecurity enhancements, including proactive system updates, employee training, and international collaboration to counter increasingly sophisticated threats. Vigilance and preparedness remain paramount in the ongoing battle against cybercrime.


