Infection Flow Diagram
Cybersecurity researchers have uncovered a sophisticated new attack attributed to APT37, a North Korean hacker group also known as ScarCruft, Reaper, and Red Eyes. Active since 2012, the group has expanded its range of targets beyond South Korea to include Japan, Vietnam, the Middle East, and organizations in the healthcare and industrial sectors.
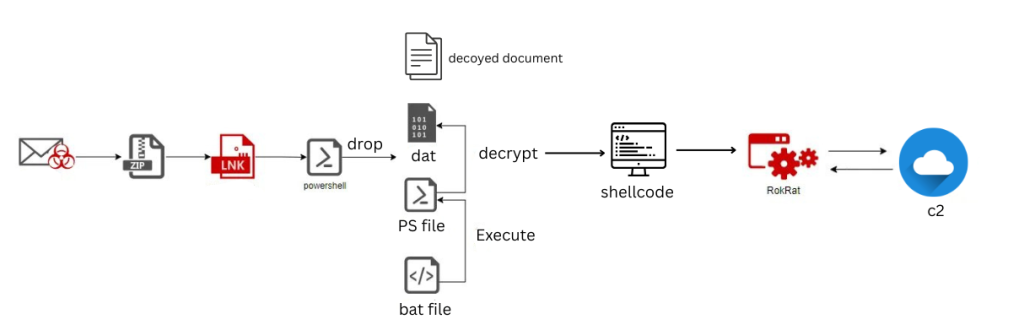
In its latest campaign, the attackers employed ZIP archives containing disguised malicious shortcuts designed to deploy the RokRat remote access trojan. According to security analyst Mohamed Ezzat from ZW01f, these files are distributed through phishing emails masquerading as documents related to trade or the political climate in North Korea. The emails appear highly convincing, as they incorporate genuine information sourced from official websites.
Upon opening the malicious shortcut (LNK), the victim triggers a sophisticated infection chain. The file contains embedded code that executes PowerShell commands to extract multiple components: a decoy HWPX document (caption.dat), an executable payload (elephant.dat), and a batch script (shark.bat). This technique allows attackers to circumvent security mechanisms that analyze only the initial file.
The “shark.bat” script subsequently executes a concealed PowerShell command, reading the contents of “elephant.dat” from a temporary directory. The script then decrypts “caption.dat” using a simple single-byte XOR key, “d,” and loads it directly into memory via Windows API functions such as VirtualProtect and CreateThread. This fileless execution method significantly reduces the likelihood of detection by antivirus systems.
The final payload, RokRat, is designed to gather extensive system intelligence, including the operating system version, hardware specifications, a list of running processes, and screen captures. To manage infected devices, the attackers leverage cloud services such as pCloud, Yandex, and Dropbox, disguising their network activity as legitimate Googlebot requests.
Despite its advanced capabilities, RokRat maintains a low detection rate. The malware incorporates multiple anti-analysis techniques, identifying virtual machines and debugging environments to hinder cybersecurity experts’ investigations. Additionally, it supports remote command execution, disk scanning, file exfiltration, and the deployment of additional modules, making it a potent tool for cyber espionage and data theft.
Modern cyberattacks are becoming increasingly sophisticated, employing fileless techniques and cloud services to evade detection. To mitigate infection risks, users must scrutinize email attachments—even from familiar sources—block script execution from email attachments, and implement behavioral threat analysis solutions.