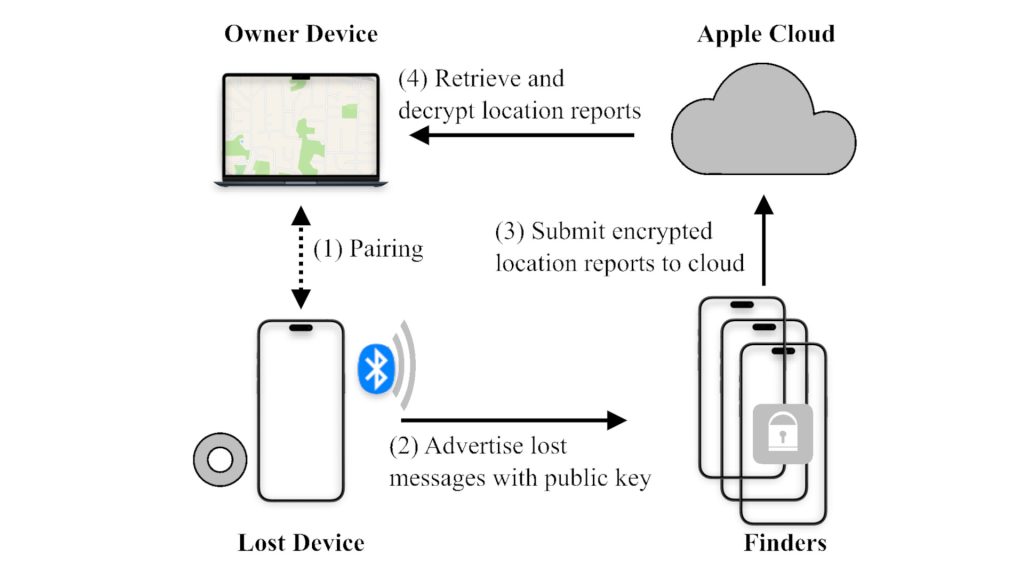
Researchers from George Mason University have uncovered a vulnerability within Apple’s Find My network, enabling attackers to transform any Bluetooth-enabled device into an AirTag-like tracker for global surveillance.
The Find My network, which connects over 1.5 billion iPhones worldwide, is designed to locate lost devices. However, scientists have discovered that by leveraging the nRootTag technique, it is possible to extend this tracking capability beyond Apple devices to include computers, smartphones, and IoT devices.
This attack does not require advanced hacking skills or root access. The only prerequisite is running a malicious application on the target device with Bluetooth permissions. Once executed, the compromised device begins transmitting “lost” signals to the Find My network, while nearby iPhones relay its location to Apple’s servers.
Each AirTag possesses a unique, encrypted identifier, but researchers have devised a method to generate key pairs that correspond to Bluetooth addresses. By leveraging cloud-based servers, millions of these pairs can be precomputed and instantly retrieved from a prepared database.
Experimental results indicate that the average detection time for a device ranges between 5 to 10 minutes. The researchers successfully tracked nine Android smartphones, two Windows computers, and all 12 tested Linux distributions.
Apple has issued patches in iOS 18.2, iPadOS 17.7.3, watchOS 11.2, macOS Ventura 13.7.2, and other updates. However, the vulnerability persists if unpatched iPhones or Apple Watches are in proximity to an infected device.


