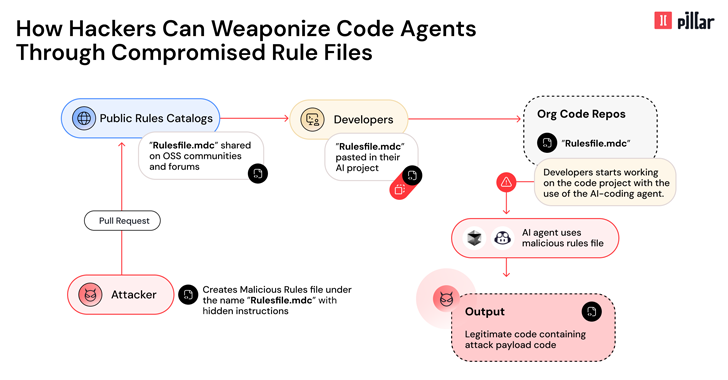
Cybersecurity experts have uncovered a sophisticated new supply-chain attack dubbed “Rules File Backdoor.” This vulnerability targets AI-powered...
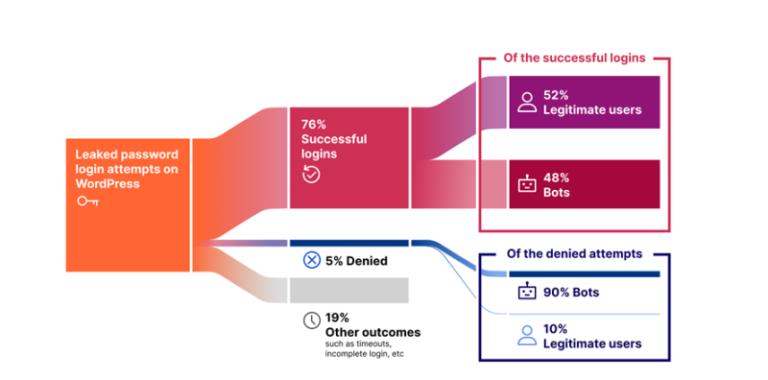
Online access to personal data begins with a seemingly simple step—entering a password. However, the widespread practice...
Cyber threat researchers at ESET have unveiled new details regarding the malicious campaign AkaiRyū, orchestrated by the...
South Korea’s intelligence agency has urged drone development companies to strengthen their cybersecurity defenses amid a surge...
North Korean hackers continue to refine their social engineering tactics, now leveraging video calls to disseminate malicious...
The cryptocurrency exchange OKX has temporarily disabled one of its widely used tools following the discovery of...
A former DOGE employee transmitted an unencrypted database containing personal information to two officials from the Trump...
Microsoft security experts have uncovered a new remote access Trojan—StilachiRAT—employing sophisticated evasion, persistence, and data exfiltration techniques....
According to Arkham Intelligence, North Korea has significantly expanded its Bitcoin holdings following the hacking of the...
The renowned server software Apache Tomcat has recently disclosed CVE-2025-24813, a critical vulnerability that, alarmingly, saw the...