Despite having rejected Alphabet’s $23 billion acquisition offer last year and stating its intention to pursue an...
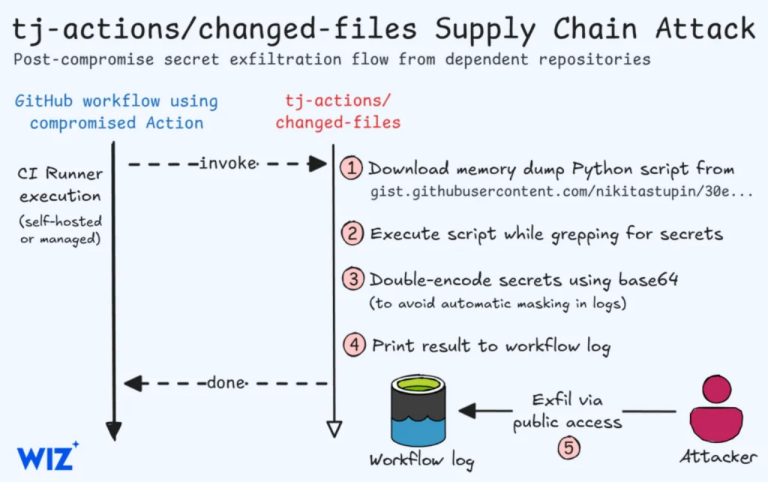
Supply chain attacks, though relatively infrequent, have the potential to cause severe and far-reaching consequences whenever they...
Cyver Core (Cyver BV) reports business results for cybersecurity teams leveraging automation with GenAI. “Cyver Core delivered a...
The China’s Ministry of State Security (MSS) issued a declaration revealing the identities of four members of...
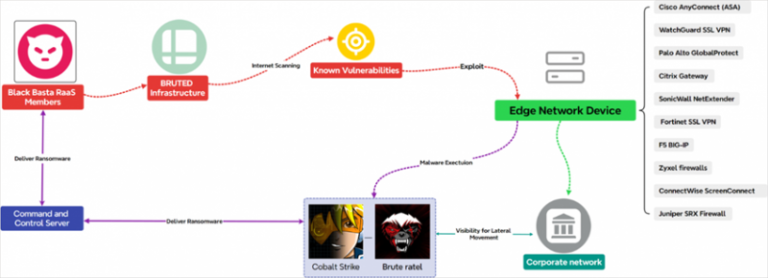
The Black Basta cybercriminal group has introduced a new tool for breaching network devices, known as BRUTED....
Akamai SIRT specialists have uncovered a vulnerability within Edimax products actively exploited to enlist IoT devices into...
Rostislav Panev has been formally charged with participating in the operations of the LockBit ransomware group. According...
American lawmakers have expressed concern over the possibility that the British government might compel U.S. tech companies...
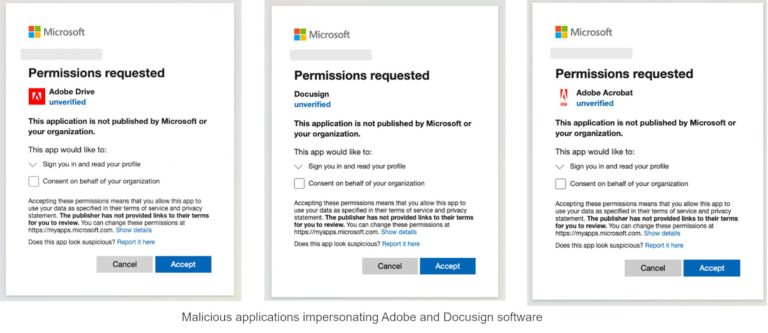
Researchers from Proofpoint have identified a sophisticated cyber campaign wherein attackers are propagating malicious OAuth applications by...
Cybersecurity researcher Yohanes Nugroho has created a sophisticated decryption tool capable of restoring files encrypted by the...