Security researcher has successfully executed the first documented attack on Passkey authentication, exploiting a patched vulnerability in mobile browsers.
Security updates addressing this flaw have been released across all major browsers: Chrome and Edge received patches in October 2024, Safari in January 2025, and Firefox in February 2025. The vulnerability has been cataloged as CVE-2024-9956.
Despite the success of the attack, Rigi’s research underscores that Passkeys remain significantly more secure than traditional password-based logins and even multi-factor authentication (MFA). However, his findings also confirm that Passkeys are not impervious to exploitation, though their attack surface is more constrained and requires specialized conditions, making them far more resistant to traditional phishing techniques.
The attack necessitated the physical placement of a hardware device within Bluetooth Low Energy (BLE) range, which extends up to 100 meters. A malicious actor could conceal a Raspberry Pi inside a backpack, using it to deploy a local web server and initiate an authentication request via Passkey.
One attack scenario involved the creation of a rogue Wi-Fi hotspot at an airport. A potential victim, upon connecting to the network, would be presented with a social media login page, where Passkey authentication was offered as an alternative to password entry. Once the victim attempted to authenticate, the attacker’s BLE-enabled device would intercept and relay a WebAuthn request, impersonating the user.
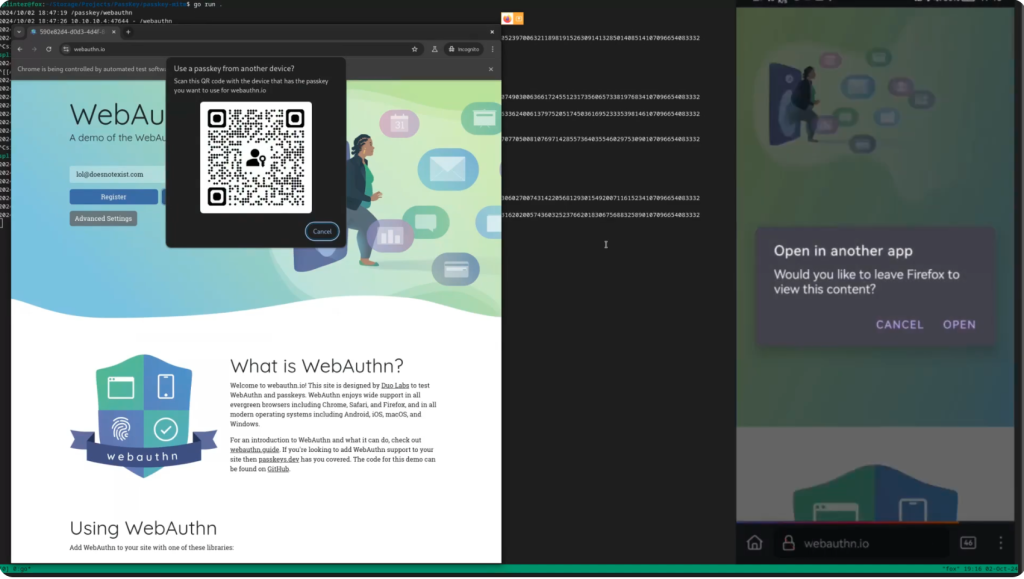
Under normal conditions, the user would be required to scan a QR code to authenticate. However, Rigi discovered that the QR code contained an embedded FIDO:/ link, which could be extracted and directly forwarded to the victim, bypassing the need for a scan. Consequently, the victim would unwittingly complete the authentication process, effectively granting the attacker access to their account.
The primary weakness lay in the fact that FIDO:/ links were navigable, allowing attackers to circumvent the QR code scanning requirement. The victim would remain unaware that a man-in-the-middle device had facilitated proxy authentication on their behalf.
Essentially, this attack represented an advanced variation of a Man-in-the-Middle (MitM) or Adversary-in-the-Middle (AitM) attack, adapted to exploit FIDO authentication protocols using hardware-based interception.
Rigi has confirmed that browser vendors have since mitigated the issue by blocking navigation via FIDO:/ URIs, preventing this specific attack vector from being replicated in the future.


