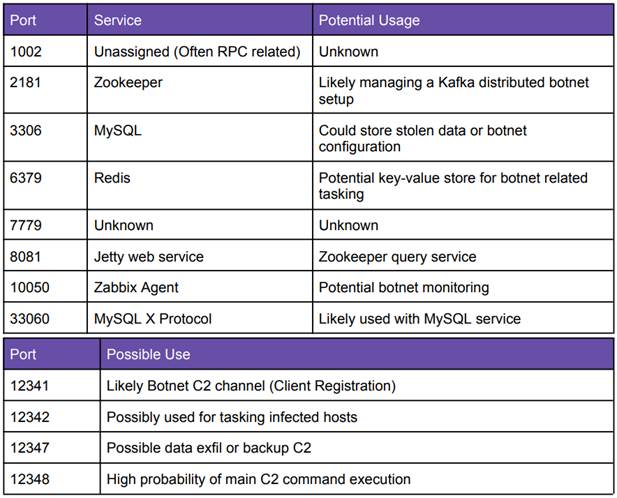
Ports used to control the botnet
Cybersecurity experts at SecurityScorecard report that a vast botnet comprising over 130,000 compromised devices is actively conducting password spraying attacks against Microsoft 365 accounts worldwide. The attack exploits the legacy Basic Authentication (Basic Auth) mechanism, enabling threat actors to bypass Multi-Factor Authentication (MFA).
Cybercriminals leverage stolen credentials obtained via keyloggers, executing the attack through non-interactive login attempts utilizing Basic Auth, thereby evading standard security mechanisms.
Experts caution that organizations relying solely on interactive login monitoring remain vulnerable. Non-interactive authentication, commonly employed for service connections and outdated protocols (such as POP, IMAP, and SMTP), often does not require MFA verification. Despite Microsoft’s gradual deprecation of Basic Auth, it remains enabled in certain enterprise environments, making it an attractive target for attackers.
Basic Auth is particularly susceptible to brute-force attacks, allowing adversaries to systematically test compromised or commonly used passwords. If a password is successfully guessed, MFA is never triggered, granting attackers direct account access without additional verification. Furthermore, this technique circumvents Conditional Access Policies, rendering the attack nearly invisible to security teams.
Once credentials are compromised, attackers can infiltrate legacy services that lack MFA support or leverage stolen credentials for subsequent phishing campaigns, potentially achieving full account takeover. Indicators of compromise (IoCs) can be found in Entra ID logs, with warning signs including:
- A surge in non-interactive login attempts
- Numerous failed authentication attempts from diverse IP addresses
- Log entries containing the user-agent “fasthttp”
Researchers suspect that the botnet may be linked to Chinese threat groups, although conclusive attribution remains uncertain. The attack’s scalability is enhanced by distributing login attempts across an extensive range of IP addresses, complicating detection and mitigation efforts.
The botnet is controlled via six Command-and-Control (C2) servers, hosted within Shark Tech’s infrastructure in the United States, while malicious traffic is routed through UCLOUD HK (Hong Kong) and CDS Global Cloud (China). The C2 servers utilize Apache Zookeeper and Kafka, with system timezones configured to Asia/Shanghai. Uptime logs indicate that the botnet has been active since December 2024.
Security experts strongly advise organizations to:
- Immediately disable Basic Authentication in Microsoft 365
- Block the IP addresses listed in the report
- Enforce Conditional Access Policies to restrict unauthorized login attempts
- Enable MFA for all accounts and rigorously monitor suspicious login activity via Entra ID
As threat actors continue to exploit legacy authentication mechanisms, organizations must proactively strengthen security controls to mitigate evolving cyber threats.