Cybersecurity researchers have uncovered a large-scale phishing campaign in which threat actors are leveraging malicious PDF documents, hosted on popular online platforms, to distribute malware.
Experts at Netskope have identified 260 unique domains hosting approximately 5,000 PDF files embedded with phishing pages. According to the company’s report, attackers are employing SEO optimization techniques to enhance the visibility of these malicious pages in search engine results.
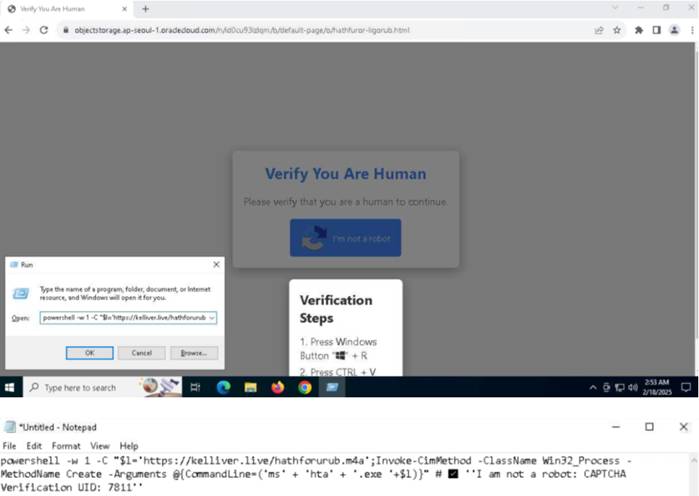
While phishing pages typically aim to steal bank card details, this campaign employs fraudulent CAPTCHA challenges within PDF files to lure users into executing malicious PowerShell commands. As a result, victims inadvertently download Lumma Stealer, an infostealer capable of exfiltrating a broad spectrum of sensitive data from infected Windows systems.
Lumma Stealer operates under the Malware-as-a-Service (MaaS) model, providing cybercriminals with sophisticated tools to harvest data from compromised devices. In early 2024, the malware’s operators integrated a proxy module known as GhostSocks, developed in Go, significantly enhancing its functionality.
According to Infrawatch, this new feature enables threat actors to convert infected devices into proxy servers, circumventing geolocation restrictions and IP-based security checks. This capability poses a heightened risk to financial institutions and other high-value targets, as it facilitates account takeovers using stolen credentials obtained via infostealers.
Security analysts estimate that this phishing campaign has affected over 1,150 organizations and more than 7,000 users since mid-2024. The primary victims include companies in North America, Asia, and Southern Europe, particularly those operating in the technology, financial services, and industrial sectors.
Of the 260 domains hosting these malicious PDF files, a significant portion is associated with Webflow CDN. Additionally, the attackers have exploited hosting services from GoDaddy, Strikingly, Wix, and Fastly. Some of these PDFs have also been uploaded to public online libraries and repositories, including PDFCOFFEE, PDF4PRO, PDFBean, and Internet Archive, increasing their chances of appearing in search engine results.
A Multifaceted Threat Landscape
This case exemplifies how modern cyber threats are evolving, leveraging a combination of social engineering, legitimate platforms, and advanced technical tactics. The campaign’s multi-layered approach makes it particularly dangerous—not only due to its scale but also because of its sophisticated attack chain: from SEO-driven victim targeting to turning infected devices into attack infrastructure via the proxy module.
The growing prevalence of such complex cyber threats underscores the critical need for a holistic cybersecurity strategy—one that integrates advanced defense mechanisms with comprehensive user awareness programs to mitigate the risks posed by modern phishing techniques.


