The Chinese state-sponsored hacking group Salt Typhoon employs a specialized utility, JumbledPath, to clandestinely monitor network traffic and potentially intercept confidential data. Their primary targets include major U.S. telecommunications companies.
Also known as Earth Estries, GhostEmperor, and UNC2286, Salt Typhoon has been active since 2019, specializing in cyber-espionage against government agencies and telecom operators. Late last year, U.S. authorities confirmed that the group had successfully breached several of the nation’s largest telecommunications providers, including Verizon, AT&T, Lumen Technologies, and T-Mobile.
Investigations have revealed that the attackers managed to access sensitive communications involving U.S. officials and exfiltrated information related to court-authorized wiretapping requests. Between December 2024 and January 2025, the group launched attacks on more than 1,000 Cisco network devices, with a significant portion of the compromised infrastructure located in the United States, South America, and India.
Analysts at Cisco Talos determined that, in some cases, the attackers maintained a persistent foothold within the networks of telecom firms for over three years. Their primary method of infiltration was the use of stolen credentials. While there was one recorded instance of exploiting CVE-2018-0171, researchers found no evidence of zero-day vulnerabilities being leveraged in these operations.
Upon gaining access, the hackers escalated their privileges by extracting additional credentials from device configurations and intercepting authentication traffic via SNMP, TACACS, and RADIUS. They also exfiltrated network device configurations using TFTP and FTP, granting them access to account details, passwords, and network topologies.
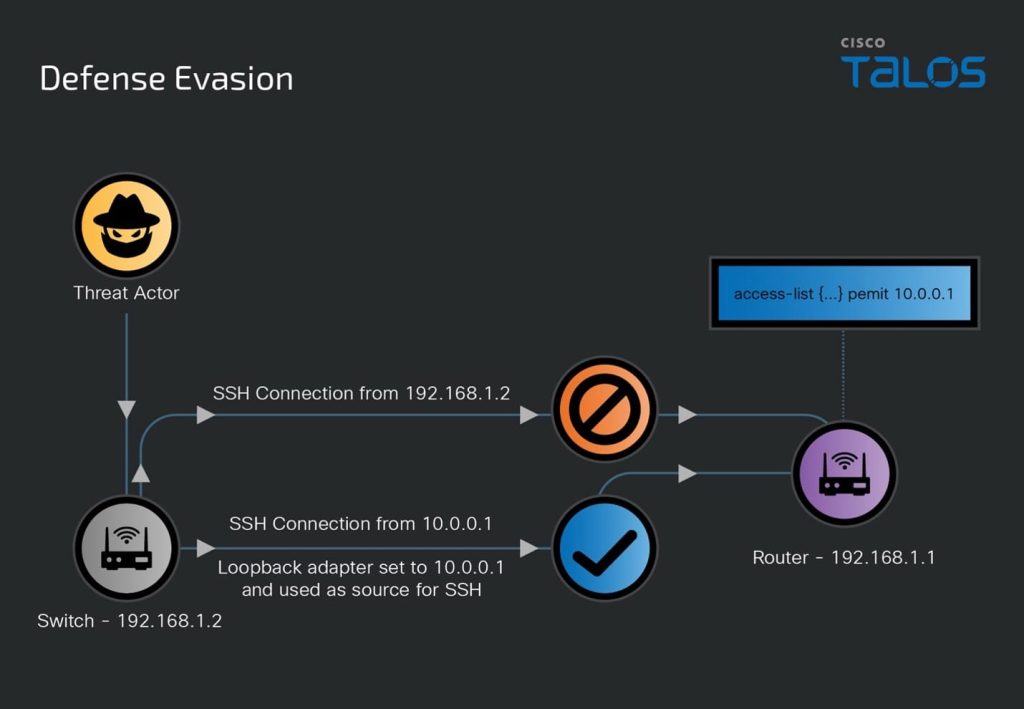
To evade detection, the attackers frequently moved laterally across network devices, leveraged compromised nodes to access additional networks, and altered router configurations. These modifications included enabling Guest Shell mode, manipulating Access Control Lists (ACLs), and creating stealthy backdoor accounts.
A key component of Salt Typhoon’s arsenal is JumbledPath, a Go-based malware designed for Linux environments and compatible with a wide range of network devices, including Cisco Nexus switches. This tool enables traffic interception from targeted devices through intermediary nodes, disguising malicious activity as legitimate operations. Additionally, JumbledPath can disable logging and erase forensic traces, complicating incident analysis.
Cisco experts advise network administrators to monitor unauthorized SSH activity on non-standard ports, anomalies in log files—such as the sudden disappearance or unusual growth of .bash_history files—as well as unexpected changes in network device configurations.
In recent years, Chinese cyber-espionage groups have intensified their focus on compromising edge network devices, deploying malware to intercept traffic, harvest credentials, and establish proxy servers for further attacks. Affected vendors include Fortinet, Barracuda, SonicWall, Check Point, D-Link, Cisco, Juniper, NetGear, and Sophos. Administrators are strongly urged to apply security updates promptly to mitigate the risk of compromise.


