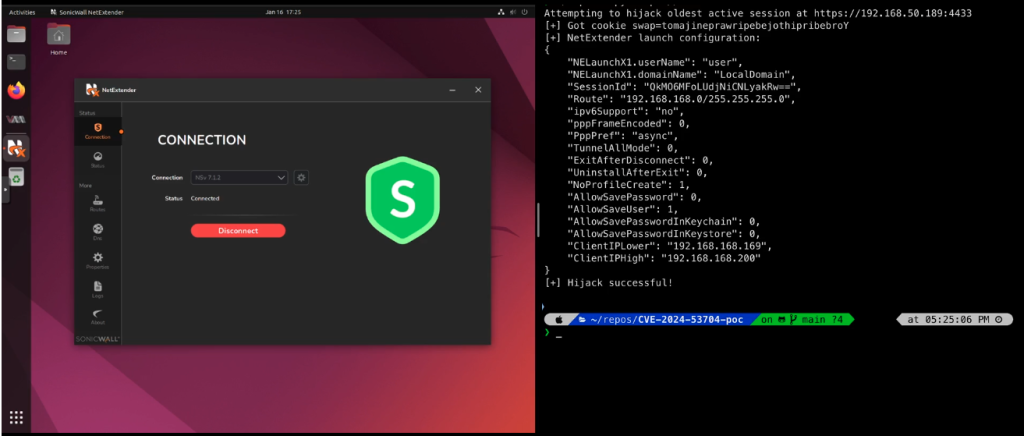
Source: Bishop Fox
Cybercriminals have swiftly begun exploiting a critical authentication bypass vulnerability in SonicWall firewalls following the public disclosure of a proof-of-concept (PoC) exploit. Tracked as CVE-2024-53704, this flaw affects the SSLVPN authentication mechanism within SonicOS versions 7.1.x (up to 7.1.1-7058), 7.1.2-7019, and 8.0.0-8035, impacting Gen 6, Gen 7, and SOHO series devices.
By leveraging this vulnerability, threat actors can hijack active SSL VPN sessions without requiring valid credentials, granting them unauthorized access to victims’ networks. SonicWall promptly notified its customers via email, urging them to apply the security update without delay. The company formally disclosed the vulnerability and released patches on January 7.
For organizations unable to immediately update their devices, SonicWall recommended temporary mitigation strategies, such as restricting access to trusted sources or completely disabling internet-facing SSL VPN functionality if it is not essential.
According to a report by Arctic Wolf, malicious actors began exploiting the flaw almost immediately after the PoC was made public. The exploit circumvents multi-factor authentication (MFA), exposes sensitive data, and disrupts ongoing VPN sessions, making it a highly potent attack vector. Security researchers caution that its ease of exploitation significantly amplifies its threat level.
The PoC exploit code was published by Bishop Fox researchers on February 10, a full month after SonicWall released its patches. However, internet-wide scans conducted on February 7 revealed that approximately 4,500 unpatched SonicWall SSL VPN servers remained exposed, highlighting the scale of the risk.
SonicWall has acknowledged that the public availability of the PoC exploit has drastically increased the likelihood of widespread attacks. The company has urged all users to immediately update affected firmware versions or disable SSL VPN access if updating is not an option.
This is not the first time SonicWall firewalls have been targeted. In October 2024, Arctic Wolf documented at least 30 intrusions that originated through SonicWall VPN remote access credentials. Notably, ransomware-affiliated groups Akira and Fog have been identified as leveraging SonicWall vulnerabilities in past campaigns.
With a proven working exploit, widespread exposure, and high-impact consequences, CVE-2024-53704 presents a serious security risk to organizations relying on SonicWall SSL VPN. Security experts strongly advise immediate patching and stringent access control measures to mitigate potential breaches.


