The MASSGRAVE research group has unveiled an exploit known as TSforge, which enables the activation of any Windows version, starting from Windows 7, as well as all editions of Microsoft Office from Office 2013 onward. This vulnerability poses a significant threat to the entire digital licensing system that has been in place within Windows since 2007.
Microsoft relies on the Software Protection Platform (SPP) to validate software licenses. Over the years, various circumvention methods have emerged, including KMS server emulation and bootloader patches. However, until now, no one had successfully breached the core activation mechanism itself. This newly discovered vulnerability allows modifications to license data without affecting the system kernel or triggering alerts from built-in security mechanisms.
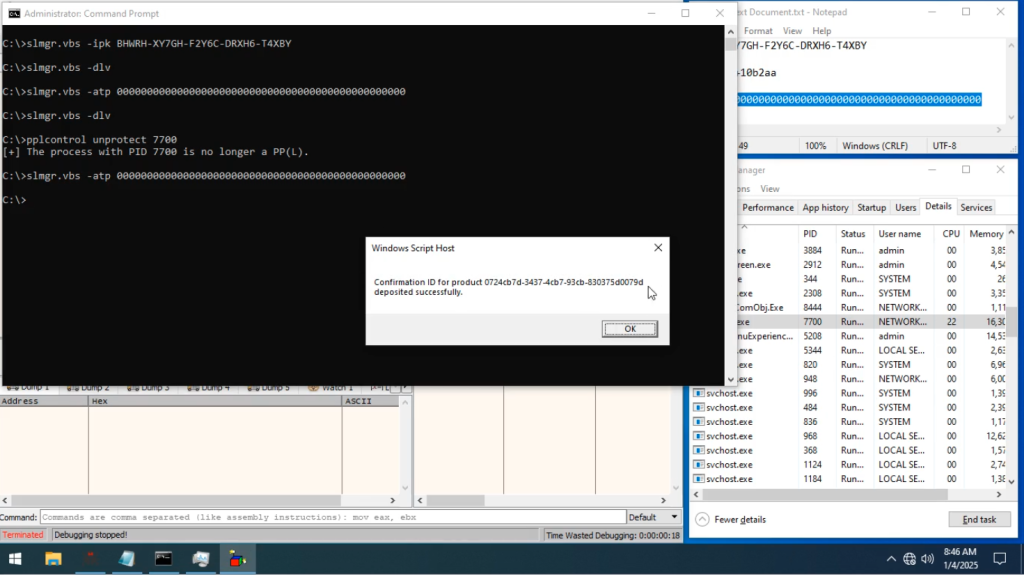
Researchers found that SPP stores license information in encrypted files—data.dat and tokens.dat—while Windows 7 uses a separate storage method. They discovered that once Windows is activated, it does not verify the validity of the stored activation data. By injecting specific values into these files, the system recognizes itself as activated—even after a reboot.
The first indications of this vulnerability surfaced in 2023, when researchers discovered that activation confirmation codes (CID) could be forged, making it possible to activate Windows and Office without connecting to Microsoft’s servers. Further analysis revealed that the key authentication mechanism fails to validate data once it has been written. The MASSGRAVE team decrypted activation keys, compared them with previous Windows versions, and successfully replicated the bypass across all modern Windows systems.
TSforge enables activation of any Windows version without requiring a product key, bypasses hardware-based activation restrictions, and even emulates KMS activation without a server connection. This effectively allows a single activation instance to be propagated across multiple devices without limitation.
For Microsoft, the most pressing issue is that this method does not rely on known “blacklisted” keys, which the company can typically block. The vulnerability is deeply rooted in the fundamental architecture of SPP, meaning that mitigating it may necessitate a complete overhaul of the Windows licensing system.
Microsoft has yet to issue an official statement, but it is evident that the company will be forced to take urgent countermeasures. Possible responses include strengthening cloud-based license verification, enforcing stricter account-based licensing, or eliminating local validation in favor of a server-side approach. Regardless of the strategy, the battle against unauthorized Windows activation has now entered a new and more sophisticated phase.


