Microsoft specialists have discovered that the cybercriminal group Storm-2372 is orchestrating a large-scale phishing campaign aimed at compromising Microsoft 365 accounts.
The attacks primarily target government organizations, NGOs, IT companies, defense contractors, telecommunications and energy sectors, as well as the healthcare industry across Europe, North America, Africa, and the Middle East. A defining characteristic of this campaign is the exploitation of device code phishing, a technique that allows adversaries to circumvent traditional authentication mechanisms.
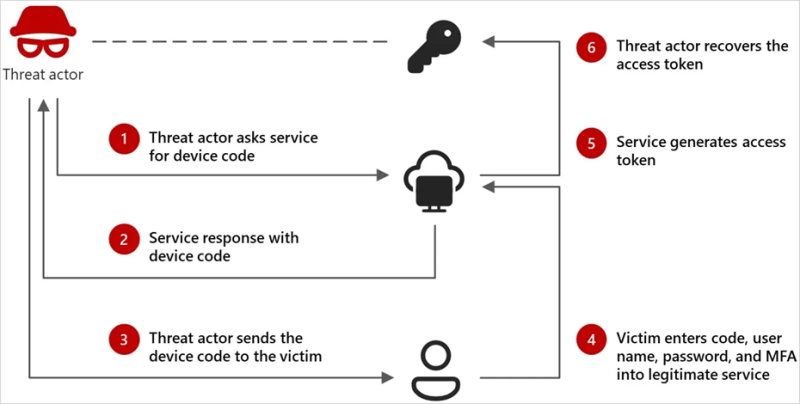
The attackers employ social engineering tactics, masquerading as influential figures to establish trust with their victims via WhatsApp, Signal, or Microsoft Teams. The adversary sends a fraudulent invitation to an online meeting, pre-generating a device code for login. Once the victim enters the code on the official Microsoft authentication page, the cybercriminals obtain a valid access token.
By leveraging this method, the attackers gain access to Microsoft 365 accounts without requiring a password. This allows them to extract emails, cloud-stored files, and other corporate data as long as the stolen tokens remain active.
Furthermore, Storm-2372 exploits the Microsoft Graph API, conducting targeted searches across compromised inboxes using keywords such as “password,” “administrator,” “TeamViewer,” “AnyDesk,” “credentials,” “secret,” “ministry,” and “gov.” Once sensitive correspondence is identified, it is exfiltrated in bulk.
Microsoft has observed a new phase of the attack, wherein adversaries utilize the Microsoft Authentication Broker client ID to generate new access tokens, ensuring prolonged persistence within the compromised environment. This also enables the attackers to register additional devices in Entra ID, facilitating further exploitation of the network.
To prevent compromise, Microsoft urges organizations to adopt the following security measures:
- Disable device code authentication wherever feasible.
- Enforce Conditional Access policies in Entra ID to restrict access exclusively to trusted devices or networks.
- Immediately revoke stolen tokens upon detecting phishing attempts by executing the revokeSignInSessions command.
- Implement additional reauthentication requirements for suspicious users.
- Monitor Entra ID for anomalous activity, paying close attention to spikes in login attempts, sign-ins from unfamiliar IP addresses, and unexpected device code requests.
Additionally, users should exercise caution when logging in from unknown devices and refrain from entering authentication codes outside official Microsoft channels.
Microsoft continues to closely monitor Storm-2372’s activities and proactively notifies organizations of potential compromises. Security experts emphasize that device code phishing represents an emerging and formidable threat, necessitating stricter access controls and continuous authentication event monitoring across corporate networks.