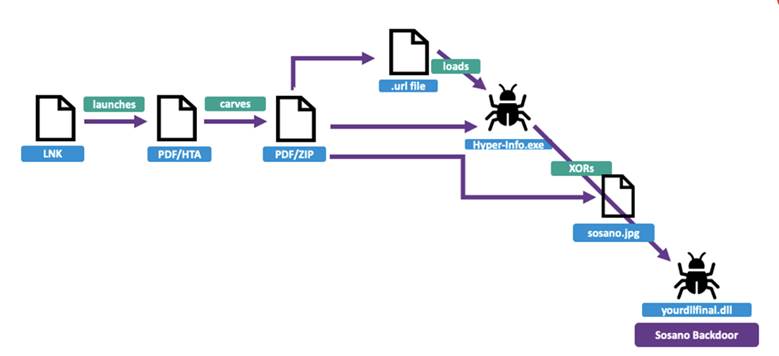
Sosano Infection Chain (Proofpoint)
Proofpoint specialists have uncovered a new targeted phishing campaign aimed at fewer than five organizations in the UAE. The attack specifically targeted companies operating in the aviation and satellite communications sectors, with the objective of deploying a previously unknown backdoor, Sosano, written in Go.
Proofpoint, which detected the activity in late October 2024, assigned the threat actor the codename UNK_CraftyCamel. One of the most distinctive aspects of the attack was the use of a compromised account belonging to the Indian company INDIC Electronics, which had established trusted business relations with the victims. The phishing emails contained links to a fraudulent domain mimicking the company’s website (“indicelectronics[.]net”), where a ZIP archive housing malicious files was hosted.
The archive contained three files: an XLS file masquerading as an Excel document and two PDF files that turned out to be polyglots. One of these files included an embedded HTA script, while the other concealed a ZIP archive within. The attackers leveraged these files to evade threat detection mechanisms and execute malicious code.
The attack sequence unfolded as follows: an LNK file within the archive triggered the command-line interface (cmd.exe), which in turn launched mshta.exe to execute the HTA script embedded in the PDF file. This script then extracted the ZIP archive from the second PDF, which contained an internet shortcut that activated a binary file. Ultimately, this led to the download of images embedding an XOR-encrypted payload. The payload was decrypted using the string “234567890abcdef,” culminating in the execution of the Sosano backdoor.
The Sosano backdoor possesses various functionalities for interacting with a C2 server and executing commands, including:
- sosano – Retrieves or changes the current directory
- yangom – Lists directory contents
- monday – Downloads and executes the next stage of the attack
- raian – Deletes a directory
- lunna – Executes shell commands
Researchers noted that the techniques employed in this campaign do not align with those of any known threat groups. However, analysis suggests a potential link to Iran, specifically the Islamic Revolutionary Guard Corps (IRGC). The selection of targets—aviation, satellite communications, and the UAE’s critical transportation infrastructure—strongly indicates an effort to gather intelligence in strategically significant sectors.
Proofpoint experts emphasized that the campaign is characterized by its small scale and highly selective targeting. The advanced evasion techniques and the compromise of a trusted third party highlight the sophistication and meticulous planning behind this attack.


