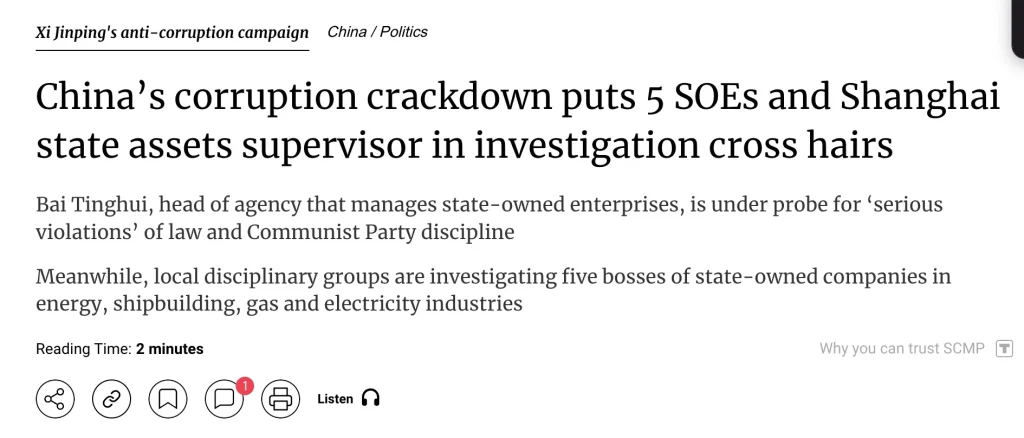
News coverage on Bai Tinghui’s investigation (Source)
SentinelLABS analysts have uncovered a data leak from the Chinese cybersecurity firm TopSec, exposing intricate details about web content monitoring systems used for censorship on behalf of both state and private clients.
The leaked documents reveal that TopSec provided specialized services to a state-owned enterprise just as its executive became the subject of a corruption investigation. This discovery underscores the close collaboration between Chinese authorities and private cybersecurity firms in managing information crises.
The breach includes over 7,000 lines of logs and code related to the configuration of DevOps infrastructure and client services. Among the leaked materials are scripts that establish connections with Chinese government domains, academic institutions, and news websites, suggesting that TopSec plays a role in China’s internet surveillance system.
The documents also list TopSec’s clients, including the Shanghai Disciplinary Inspection Commission, the Gucheng County Petitions Bureau, and the Center for Combating Illegal Information. Furthermore, records indicate collaboration with the Ministry of Public Security on monitoring projects in Shanghai and Dandong.
Additionally, the leak reveals the use of the Sparta system, which detects “sensitive” keywords flagged for censorship. When such terms are identified, real-time alerts are transmitted to corporate WeChat chats, illustrating the deep integration of TopSec into state-driven internet censorship mechanisms.
Notably, on the same day reports of suspicious content were dispatched via WeChat, authorities launched an investigation into Bai Tinghui, the head of the Shanghai State-Owned Assets Supervision and Administration Commission. Soon after, the Chinese government confirmed the inquiry, and his name swiftly vanished from most official sources.
Founded in 1995, TopSec specializes in monitoring, IT security, and cloud services. The company owns over 1,000 patents, 87 software copyrights, and operates 12 subsidiaries. TopSec is also believed to provide authorities with software vulnerabilities for exploitation in state-led intelligence operations. According to its annual report, TopSec’s cloud services extend across all 31 administrative regions of China.
Experts note that while cybersecurity cooperation between governments and private firms is common in many countries, China’s model demonstrates a far deeper level of integration. This incident highlights the critical importance of log management and credential security to prevent data leaks of this magnitude.
Separately, reports have surfaced about a security vulnerability in the widely used surveillance apps Cocospy and Spyic, compromising the personal data of millions of users. The flaw also exposes the email addresses of customers who registered for these services to install spyware on their victims’ phones. While the origins of Cocospy and Spyic remain unclear, an analysis of their infrastructure suggests possible ties to the Chinese company 711.icu.