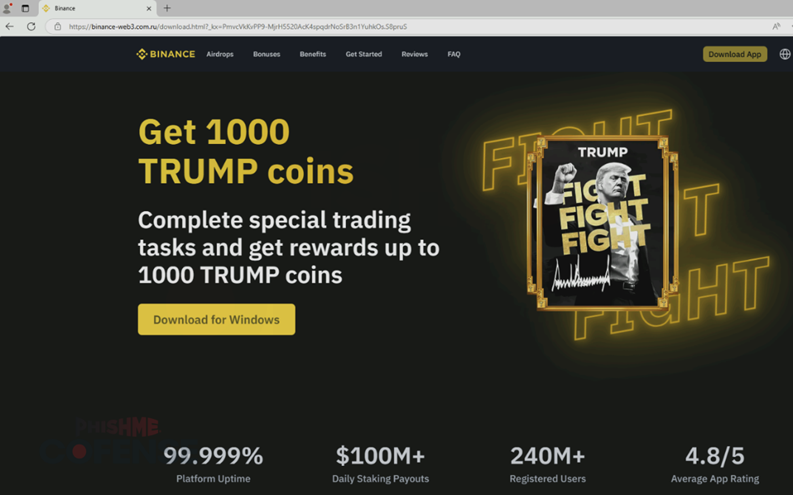
Hackers have launched a phishing campaign aimed at deploying the ConnectWise RAT trojan onto victims’ computers. Fraudulent emails, purportedly from Binance, entice users with the opportunity to acquire newly issued Donald Trump tokens.
The emails promise recipients the chance to earn TRUMP tokens by installing Binance software, registering an account, and funding their balance. However, instead of receiving the promised cryptocurrency, victims inadvertently download ConnectWise RAT—a remote access trojan that grants cybercriminals full control over infected devices.
Experts at Cofense have reported that while they cannot definitively attribute the attack to a specific threat actor, the perpetrators are actively monitoring infections. In fact, they can establish a connection to a victim’s computer in under two minutes after the malware is installed.
ConnectWise RAT has gained popularity among cybercriminals due to its extensive functionality, free availability, and ease of configuration. Analysts have noted that similar campaigns in the past have leveraged counterfeit emails impersonating LinkedIn, Binance, Virtru, and even the U.S. Social Security Administration. The primary challenge in mitigating these attacks lies in the fact that ConnectWise RAT is considered a legitimate tool, making it difficult to block its files without disrupting lawful installations.
The phishing emails meticulously mimic Binance’s branding, incorporating the company’s name in the sender field and even including risk warnings to enhance credibility. The phishing website, linked within the email, is highly convincing, featuring authentic visuals sourced from Binance’s official site and the TRUMP token. It is through this fraudulent portal that the RAT trojan is surreptitiously delivered to the victim’s device.
Once the infection takes hold, the attackers swiftly establish remote access to the compromised computer. Unlike traditional ConnectWise RAT attacks, where hackers often adopt a stealthy approach before engaging in malicious activity, this campaign demonstrates an immediate focus on extracting stored credentials, particularly from the Microsoft Edge browser.
Cofense emphasized that the accessibility of ConnectWise RAT makes it an attractive tool for both novice fraudsters and sophisticated APT groups seeking to obscure their operations. The firm has already detected multiple phishing campaigns utilizing ConnectWise RAT throughout 2025.


