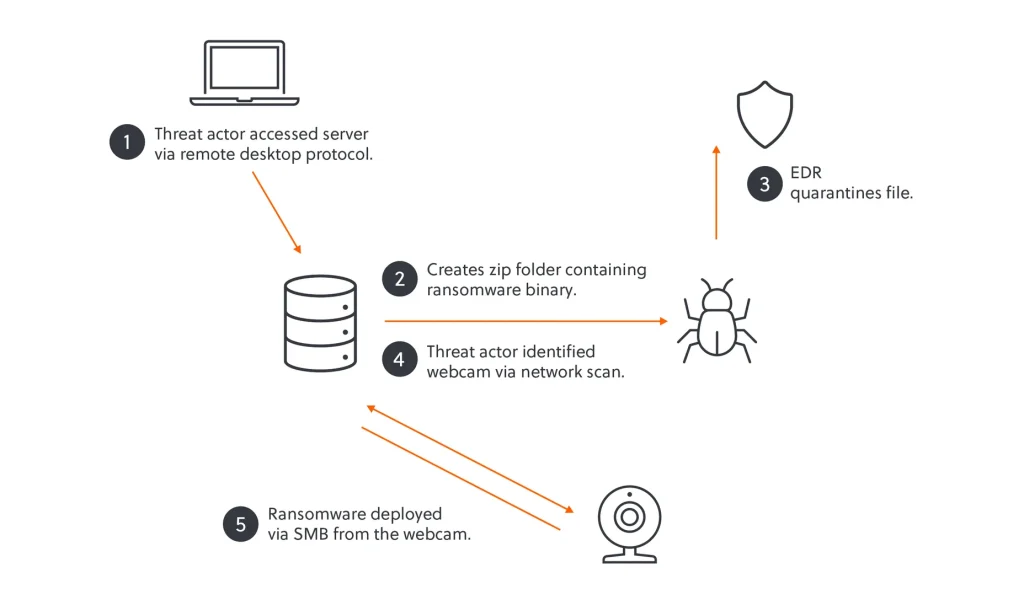
The Akira ransomware group employed an unconventional attack vector, leveraging an unsecured webcam to bypass security defenses and encrypt data across the victim’s network. This ingenious tactic enabled the cybercriminals to circumvent Endpoint Detection and Response (EDR) mechanisms, which had initially blocked the execution of the ransomware on Windows systems.
According to S-RM cybersecurity experts, the attackers gained entry into the corporate network by exploiting a vulnerability in remote access protocols. To breach credentials, they likely relied on stolen login data or brute-force attacks. Once inside, the hackers deployed the legitimate remote access tool AnyDesk, allowing them to move laterally across the network and expand their foothold.
The ransomware operators initially attempted to execute a malicious payload concealed within an archive file, but the victim’s security system successfully detected and neutralized it. Rather than abandoning the attack, the adversaries pivoted to an alternative infiltration method.
They scanned the network for exploitable devices that could facilitate security bypasses—ultimately identifying an internet-connected webcam running on Linux.
The compromised webcam presented a critical weakness:
- It was remotely accessible and lacked an installed EDR agent.
- Its operating system supported the Linux variant of Akira ransomware.
Recognizing this vulnerability, the attackers gained access to the webcam, used it to mount SMB shares on Windows systems, and initiated the encryption process on network drives. As a result, they effectively circumvented security defenses and encrypted crucial files on the victim’s servers.
S-RM analysts emphasized that the webcam had available firmware updates that could have patched the vulnerability, but they had not been installed—ultimately enabling the breach.
This incident underscores a critical flaw in security strategies: EDR protection alone cannot guarantee comprehensive security if vulnerable IoT devices remain within the network.
To mitigate such risks, organizations must:
- Ensure all devices receive timely firmware updates to address known vulnerabilities.
- Isolate IoT devices from mission-critical network segments to prevent lateral movement by attackers.
The Akira ransomware attack serves as a stark reminder that even seemingly insignificant devices can serve as entry points for sophisticated cyberattacks if left unprotected.


