The Vo1d botnet, which targets Android TV devices, continues to evolve at a remarkable pace, having already infected over 1.5 million devices across 226 countries. According to XLab, the botnet is employed to orchestrate anonymous proxy networks and reached its zenith on January 14, 2025, with approximately 800,000 active bots at that time.
Experts at Dr. Web first documented a large-scale Vo1d attack in September 2024, detecting 1.3 million infected devices in 200 nations. This latest campaign, however, indicates that the botnet has only broadened its reach since being exposed.
The developers of Vo1d have incorporated sophisticated protective measures, including RSA encryption, a customized XXTEA algorithm, and a fault-tolerant infrastructure reliant on domain generation algorithms (DGA). These features significantly hamper efforts to detect and dismantle the botnet.
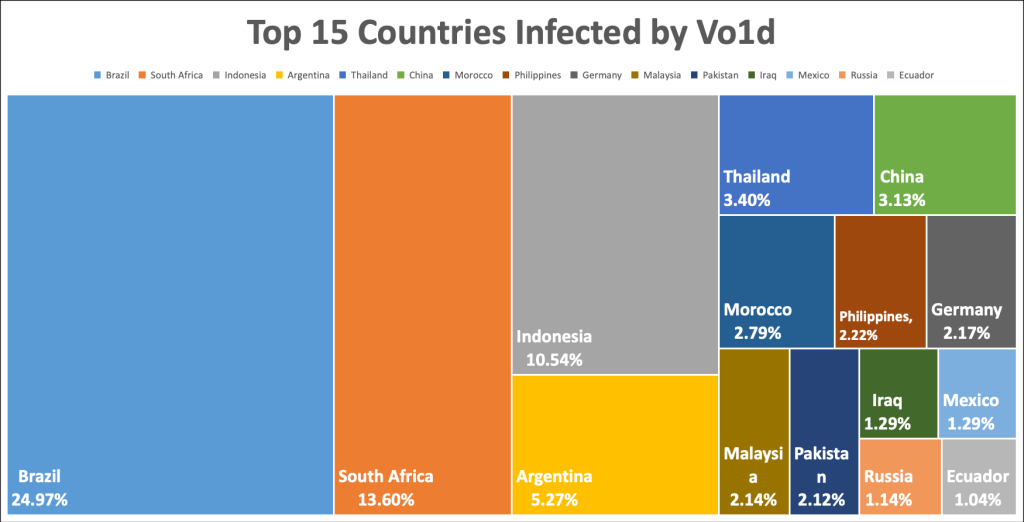
Surpassing numerous well-known botnets—Bigpanzi, Mirai, and the one behind the record-breaking 5.6 Tbps DDoS attack of 2024—Vo1d ranks among the largest in recent years. Brazil leads in infections, with 25%, followed by South Africa (13.6%), Indonesia (10.5%), Argentina (5.3%), Thailand (3.4%), and China (3.1%). India experienced a particularly dramatic surge over three days, with infected devices soaring from 3,900 to 217,000.
Researchers at XLab attribute these spikes to a “rental-return” system, wherein Vo1d leases its botnet infrastructure to other groups operating in specific regions. The 911 S5 service, which faced sanctions by the U.S. Department of Justice in 2024, reportedly used a similar arrangement.
XLab’s proxy leasing mechanism ostensibly functions in two phases:
- • Leasing Phase: At the start of the lease period, bots are diverted from the main Vo1d network to carry out the renter’s operations, causing a sudden drop in the number of infected devices in Vo1d’s active pool as bots temporarily leave its control.
- • Return Phase: When the rental term ends, the bots return to the Vo1d network. This reintegration triggers a sharp rise in the number of infected devices, as the bots once again operate under Vo1d’s aegis.
The botnet’s command and control (C2) infrastructure is equally formidable: 32 seed values for the domain generation algorithm (DGA) produce more than 21,000 C2 domains. Communication between bots and C2 servers is secured via a 2048-bit RSA key, making it impossible to intercept or spoof commands even if a domain is identified.
In addition to creating anonymous proxy networks, Vo1d is also employed for click fraud and artificial advertisement views. By emulating user activity, it generates clicks and impressions for fraudulent advertisers. Special plugins that simulate human behavior and the Mzmess SDK platform, which distributes tasks among the bots, contribute to this deception.
Although Vo1d’s reach is extensive, Android TV users can reduce the likelihood of infection by adhering to several basic security measures:
- Purchase devices from reputable manufacturers and official sellers, lowering the risk of preinstalled malware.
- Install firmware and security updates regularly, ensuring vulnerabilities exploited by attackers are promptly addressed.
- Avoid installing applications from sources other than Google Play, as third-party stores or custom firmware significantly increase the chance of infection.
- Disable remote access if it is not in use, preventing unauthorized manipulation.
- Isolate IoT devices by placing Android TV on a separate network to safeguard other devices that contain sensitive information.
Despite its status as one of the most formidable threats to Android TV devices, it remains unclear what new infection tactics Vo1d’s operators might deploy. Nonetheless, a vigilant approach to cybersecurity can markedly reduce the odds of becoming part of this malicious network.


