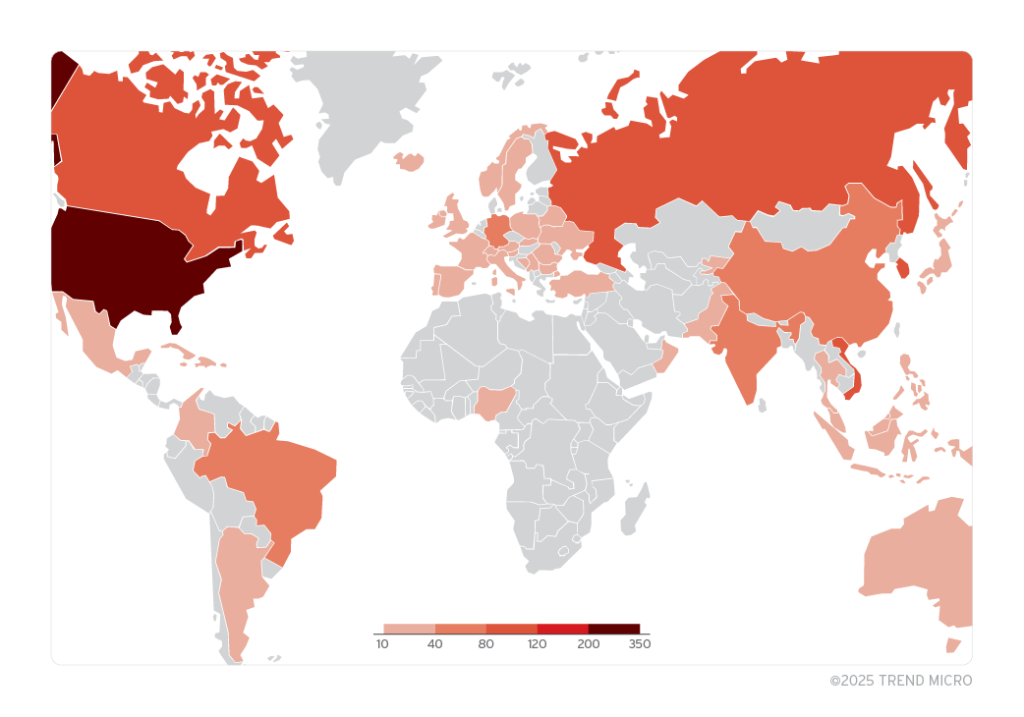
Files exploiting ZDI-CAN-25373 countries by file submission origin | Image: Trend Micro
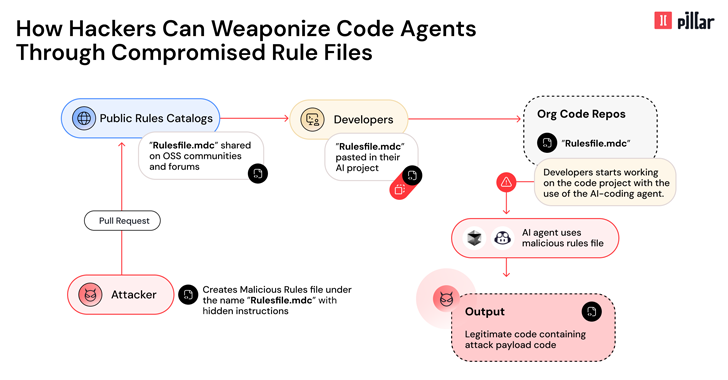
An unpatched vulnerability in Microsoft Windows, tracked as ZDI-CAN-25373, is being actively exploited by eleven state-sponsored threat actors, including groups linked to China, Iran, and North Korea. These malicious entities have leveraged the vulnerability since 2017 to orchestrate cyber-espionage campaigns, data theft, and financially motivated cyber-attacks.
According to detailed research by Trend Micro’s Zero Day Initiative (ZDI), this flaw resides within Windows Shortcut (.LNK) file handling, enabling attackers to covertly execute malicious commands on targeted systems. The primary technique for circumventing security controls involves embedding hidden command-line arguments using Line Feed (\x0A) and Carriage Return (\x0D) characters.
To date, approximately 1,000 malicious .LNK files have been identified, associated with various Advanced Persistent Threat (APT) groups, including Evil Corp (Water Asena), Kimsuky (Earth Kumiho), Konni (Earth Imp), Bitter (Earth Anansi), and ScarCruft (Earth Manticore). Significantly, half of these threat actors are tied directly to North Korea, indicating a coordinated offensive effort within the DPRK’s cyber operations.
The attacks primarily target governmental institutions, financial entities, telecommunications firms, think tanks, and military organizations across the United States, Canada, Russia, South Korea, Vietnam, and Brazil. Among the malware deployed in these operations are Lumma Stealer, GuLoader, Remcos RAT, and the propagation of Raspberry Robin malware, specifically linked to Evil Corp.
Despite the severe risks posed, Microsoft has classified this vulnerability as low-severity and has indicated no immediate intention to release a patch. Security experts caution that the absence of remediation leaves organizations dangerously exposed, enabling attackers to clandestinely exfiltrate critical information undetected by end-users.